Other Parts Discussed in Thread: OMAPL138, OMAP-L138, AM1808
Trying to load my program in to a secure C6748 (E) using GenericSecureUartHost.exe.
I read everything I could find here.
This is the response from the loader:
(File IO): Read 149516 bytes from file C:\Projects\CCS\OMAPL138_C6748_Generic_Security\OMAP-L138_Secure\GNU\AISUtils\MXS_Gmbl.bin.
(Serial Port): Opening COM4 at 115200 baud...
(AIS Parse): Read magic word 0x41504954.
(AIS Parse): Waiting for BOOTME... (power on or reset target now)
(AIS Parse): BOOTME received!
(AIS Parse): Performing Start-Word Sync...
(AIS Parse): Performing Ping Opcode Sync...
(AIS Parse): Processing command 0: 0x58535920.
(AIS Parse): Performing Opcode Sync...
(AIS Parse): Secure key loading, entering secure mode.
(AIS Parse): Processing command 1: 0x58535923.
(AIS Parse): Performing Opcode Sync...
(AIS Parse): Setting boot exit mode...
(AIS Parse): Set exit mode to 0x00000000.
(AIS Parse): Processing command 2: 0x5853590D.
(AIS Parse): Performing Opcode Sync...
(AIS Parse): Executing function...
(AIS Parse): Secure mode; sending signature.
(AIS Parse): Processing command 3: 0x58535921.
(AIS Parse): Performing Opcode Sync...
(AIS Parse): Loading encoded section...
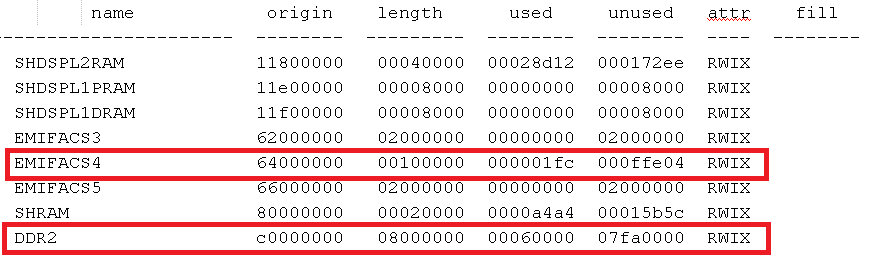
(AIS Parse): Loaded 145216-Byte section to address 0x11800000.
(AIS Parse): Processing command 4: 0x58535921.
(AIS Parse): Performing Opcode Sync...
(Serial Port): Read error: The operation has timed out.
(AIS Parse): I/O Error in read!
(Serial Port): Read error: The operation has timed out.
(AIS Parse): I/O Error in read!
(System): Boot aborted by user.
(Serial Port): Read error: The I/O operation has been aborted because of either a thread exit or an application request.
Please help.