HI,
using CPU to update the G2553 program success by BSL, but information memory maybe erased or changed. I haven't found the reason, can you give some advise.
I tried three ways:
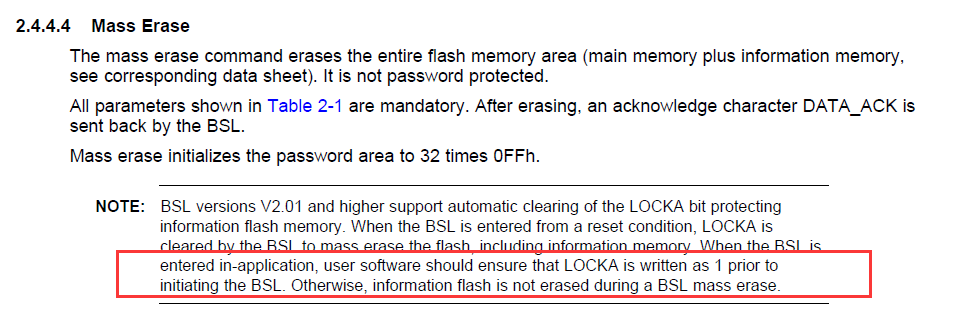
1.mass erase->send right password->send bin file data
2.send right password->Erase segment->send bin file data
2. send wrong password->send right password->send bin file data
thank!
#include <sys/stat.h>
#include <unistd.h>
#include <sys/mman.h>
#include <time.h>
#include <stdio.h>
#include <stdlib.h>
#include <fcntl.h>
#include <termios.h>
#include <errno.h>
#include <string.h>
typedef unsigned char u8;
typedef unsigned short u16;
#define MCU_ACK 0xFA
#define MCU_TEST 0xFB
#define MCU_START 0xFD
#define MCU_END 0xFE
#define MCU_TIMEOUT (-1)
#define MCU_DATA_IDX 3
#define DATA_CMD_LEN 1
#define DATA_PORT_LEN 1
#define DATA_VOLTAGE_LEN 2
#define DATA_CURRENT_LEN 2
#define DATA_VERSION_LEN 2
#define MSG_MAX_LEN 64
#define MSG_HEADER_LEN (1 + DATA_CMD_LEN + DATA_PORT_LEN)
#define MSG_END_LEN (1)
#define MSG_LEN_GET_VC (MSG_HEADER_LEN + DATA_VOLTAGE_LEN + DATA_CURRENT_LEN + MSG_END_LEN)
#define MSG_LEN_GET_VERSION (MSG_HEADER_LEN + DATA_VERSION_LEN + MSG_END_LEN)
#define MTK_GPIO_BASE 0x1E000600
#define MTK_GPIO_CTL_OFF 0
#define MTK_GPIO_WIDTH 0x100
#define MTK_GPIO_SET_OFF 0x30
#define MTK_GPIO_CLR_OFF 0x40
#define BSL_EN 16
#define BSL_RST 14
#define BSL_TEST 13
#define BSL_DEALY 60
#define MCU_MAX_BIN (64 * 1024) /* FLASH 16K */
#define UPGRADE_TRUNK 128
#define MCU_UPGRADE_FILE "/tmp/mcu-upgrade.tmp"
#define DEV_MCU_PATH "/dev/ttyS0"
#define CMD_RX_DATA_BLOCK 0x12
#define CMD_RX_PASSWORD 0x10
#define CMD_PASSWORD_LEN 0x20
#define CMD_ERASE_SEGMENT 0x16
#define CMD_ERASE_MAIN_INFO 0x16
#define CMD_MASS_ERASE 0x18
#define CMD_ERASE_CHECK 0x1C
#define CMD_TX_BSL_VER 0x1E
#define CMD_MAX_BYTES 0x104 /* �������ȣ�8+250+2 */
#define MCU_FLASH_START 0xC000 /* flash��д����ʼ��ַ */
#define BSL_SYNC 0x80
#define BSL_ACK 0x90
#define BSL_NAK 0xA0
#define BSL_RECEIVE_TIEMS 10
#define CMD_RETRY_TIME 3
enum {
MCU_CMD_PORT_CONTROL = 1, //power on/off one port
MCU_CMD_SET_SYS_POWER = 2,
MCU_CMD_GET_PORT_STATUS = 3,
MCU_CMD_GET_VC = 4,
MCU_CMD_GET_PD_CLASS = 5,
MCU_CMD_GET_ALL = 6,
MCU_CMD_GET_VERSION = 7,
MCU_CMD_ALLPORTS_CONTROL = 8, //power on/off all ports
MCU_CMD_MAX,
};
static int mcu_bsl_sync(void)
{
u8 cmd_buf[1];
int ret, retry_time = 0;
int recvtimes, flag;
retry_sync:
recvtimes = 0;
flag = 0;
/* send 0x80 */
cmd_buf[0] = BSL_SYNC;
mcu_send_msg(cmd_buf, 1);
ft_udelay(10 * 1000);
printf("%s: send BSL_SYNC\n", __func__);
do {
ret = mcu_recv_msg(cmd_buf, 1);
flag = (recvtimes++ < BSL_RECEIVE_TIEMS) &&
(ret != 1 || (cmd_buf[0] != BSL_ACK && cmd_buf[0] != BSL_NAK));
if (flag) {
ft_udelay(10*1000);
}
} while (flag);
if (ret != 1 || cmd_buf[0] != BSL_ACK) {
printf("%s: SYNC fail, ret:%d, cmd_buf[0]:0x%x\n", __func__, ret, cmd_buf[0]);
if (retry_time++ < CMD_RETRY_TIME) {
goto retry_sync;
}
return -EIO;
}
printf("%s: sync success\n", __func__);
return 0;
}
static int mcu_bsl_command(u8 cmd, u8 l1, u8 l2, u8 al, u8 ah, u8 ll, u8 lh, u8 *data, int num, int udelay)
{
u8 cmd_buf[CMD_MAX_BYTES];
int ret, retry_time = 0;
int recvtimes, flag;
ret = mcu_bsl_sync();
if (ret)
return ret;
retry:
recvtimes = 0;
flag = 0;
ret = bsl_cmd(cmd_buf, cmd, l1, l2, al, ah, ll, lh, data, num);
mcu_send_msg(cmd_buf, ret);
ft_udelay(udelay);
do {
ret = mcu_recv_msg(cmd_buf, 1);
flag = (recvtimes++ < BSL_RECEIVE_TIEMS) &&
(ret != 1 || (cmd_buf[0] != BSL_ACK && cmd_buf[0] != BSL_NAK));
if (flag) {
ft_udelay(10*1000);
}
} while (flag);
if (ret != 1 || cmd_buf[0] != BSL_ACK) {
printf("%s: %s fail, ret:%d, cmd_buf[0]:0x%x\n", __func__, bsl_cmd_name(cmd), ret, cmd_buf[0]);
if (retry_time++ < CMD_RETRY_TIME) {
ft_udelay(300*1000);
goto retry;
}
return -EIO;
}
printf("%s: %s success\n", __func__, bsl_cmd_name(cmd));
return 0;
}
int mcu_low_upgrade(u8 *bin, int size)
{
u8 password[CMD_PASSWORD_LEN], tmp_buf[CMD_MAX_BYTES];
int ret, i;
u16 start;
printf("%s: size:%d\n", __func__, size);
//send wrong password
memset(password, 0xff, CMD_PASSWORD_LEN-2);
memset(password+CMD_PASSWORD_LEN-2, 0x00, 2);
ret = mcu_bsl_command(CMD_RX_PASSWORD, 0x24, 0x24, 0, 0, 0, 0, password, CMD_PASSWORD_LEN, 10*1000);
if (ret)
return ret;
ret = mcu_bsl_command(CMD_MASS_ERASE, 0x04, 0x04, 0, 0, 0x06, 0xA5, NULL, 0, 300*1000);
if (ret)
return ret;
//send right password
memset(password, 0xff, CMD_PASSWORD_LEN);
ret = mcu_bsl_command(CMD_RX_PASSWORD, 0x24, 0x24, 0, 0, 0, 0, password, CMD_PASSWORD_LEN, 10*1000);
if (ret)
return ret;
printf("%s: start write bin\n", __func__);
start = MCU_FLASH_START;
/* start download bin */
for (i = 0; i < size; i += UPGRADE_TRUNK) {
memcpy(tmp_buf, bin+i, UPGRADE_TRUNK);
ret = mcu_bsl_command(CMD_RX_DATA_BLOCK, UPGRADE_TRUNK+4, UPGRADE_TRUNK+4,
(start+i) & 0xff, ((start+i) >> 8) & 0xff, UPGRADE_TRUNK, 0, tmp_buf, UPGRADE_TRUNK, 500*1000);
if (ret)
return ret;
printf("%s: write bin 0x%x success\n", __func__, start+i);
}
printf("%s: start write bin all success\n", __func__);
/* download over */
return 0;
}
int mcu_check_upgrade(void)
{
unsigned char version, patchlevel;
if (poe_get_version(&version, &patchlevel)) {
printf("MCU Version: unknown\r\n");
return -1;
}
printf("MCU Version: %d.%d\r\n", version, patchlevel);
return 0;
}
int mcu_upgrade_routine(void)
{
struct stat buf;
int fd, size, ret;
u8 *bin;
fd = open(MCU_UPGRADE_FILE, O_RDONLY);
if (fd < 0) {
printf("No MCU upgrade file, return!\n");
return -ENOENT;
}
memset(&buf, 0, sizeof(stat));
stat(MCU_UPGRADE_FILE, &buf);
size = buf.st_size;
if (size > MCU_MAX_BIN) {
printf("MCU upgrade bin size is %d, too big!\n", size);
close(fd);
return -EINVAL;
}
bin = malloc(size);
if (bin == NULL) {
printf("%s: malloc %d fail\n", __func__, size);
close(fd);
return -ENOMEM;
}
ret = read(fd, bin, size);
if (ret != size) {
printf("%s: read fail, size:%d, ret:%d\n", __func__, size, ret);
close(fd);
free(bin);
return -EIO;
}
close(fd);
/* first disable jtag��use gpio 13 14 15 */
ret = mcu_bsl_upgrade_start();
if (ret < 0) {
printf("mcu_upgrade_prepare fail, ret=%d\n", ret);
goto exit_upgrade;
}
ret = mcu_bsl_uart_init();
if (ret < 0) {
printf("mcu_uart_init fail, ret=%d\n", ret);
goto exit_upgrade;
}
mcu_clear();
ret = mcu_low_upgrade(bin, size);
if (ret < 0) {
printf("mcu_low_upgrade fail, ret=%d\n", ret);
goto exit_upgrade;
}
exit_upgrade:
/* MCU reset */
if (mcu_exit_bsl() < 0) {
printf("exit BSL fail\n");
return -EIO;
}
mcu_reset();
ft_udelay(300*1000);
mcu_normal_uart_init();
if (ret < 0) {
printf("MCU upgrade fail\n");
return ret;
}
ret = mcu_check_upgrade();
if (ret < 0) {
printf("mcu_check_upgrade fail, ret=%d\n", ret);
return -EIO;
}
return 0;
}
int main(int argc, char *argv[])
{
return mcu_upgrade_routine();
}