Other Parts Discussed in Thread: SYSBIOS, UNIFLASH
Tool/software: TI-RTOS
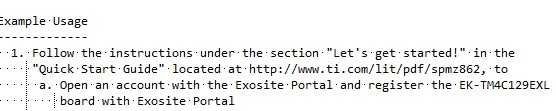
In an effort to test the whole foodchain, I've finally managed to rebuild the Out-of-Box demo for the EK-TM4C129EXL.
It's running fine; acquires its IP address via DHCP, gets time from NTP... ( there's no proxy involved, so haven't changed these settings. )
But having deleted the device on exosite - of course this requires the device to be re-activated. Debug session is correctly reporting device MAC address and CIK.
Connected via terminal, the 'activate' command doesn't seem to do anything. Should it?
Is there an easy way to effect re-activation?