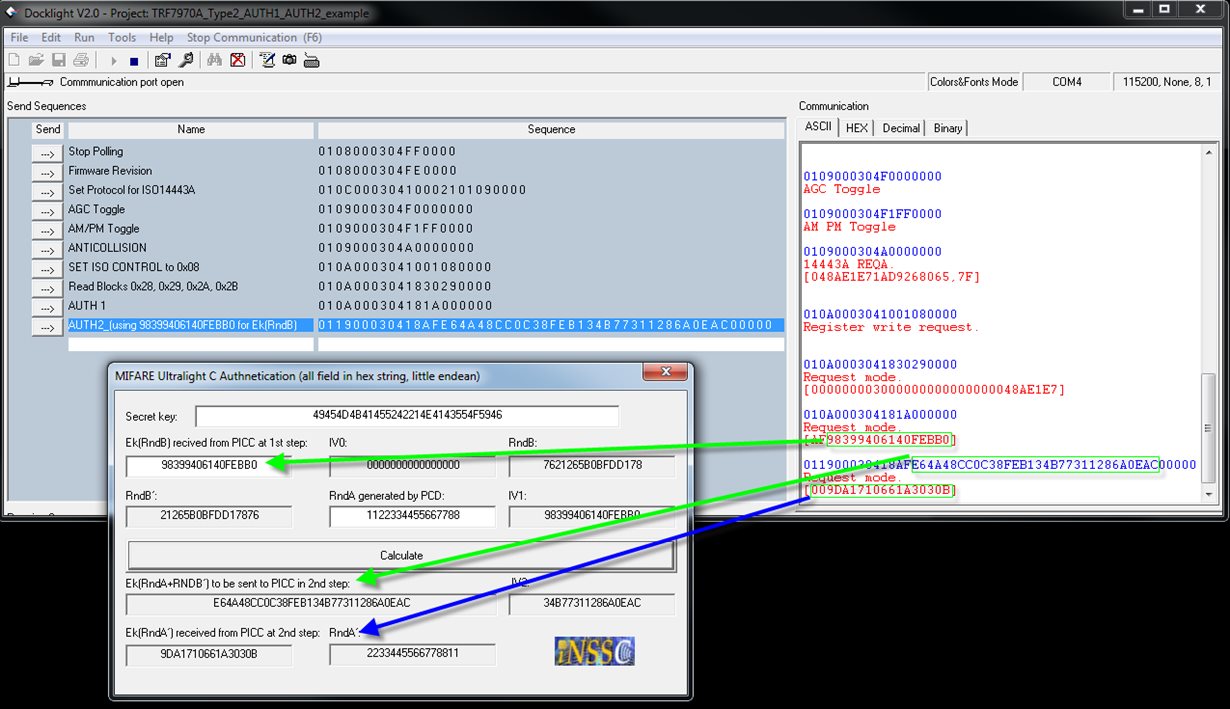
I am developing Mifare Ultralight C reader with the TRF7970A. Authentication of the card is not happening properly. The problem is when I send 1A command (for authentication part1), I am get encrypted random number.
But for part 2 authentication (i.e. for AF command) I don't get expected response instead collision is happening.
Please help me with a solution.
Thank you