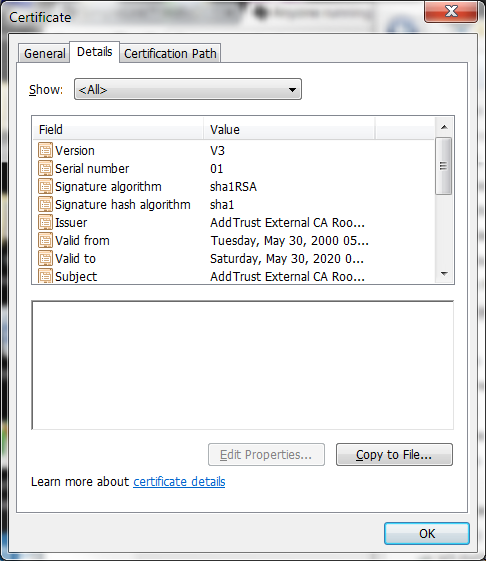
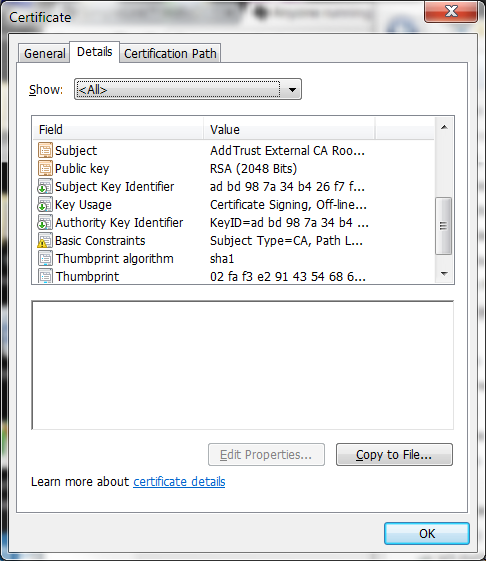
I am having some trouble with a SHA256 CA certificate, and without looking into it deeper, I cannot see any difference yet.
Can anyone recommend any tools or sites to test a SHA256 CA with the SSL example against? I figure someone has either tried this or ran into issues and solved it already.