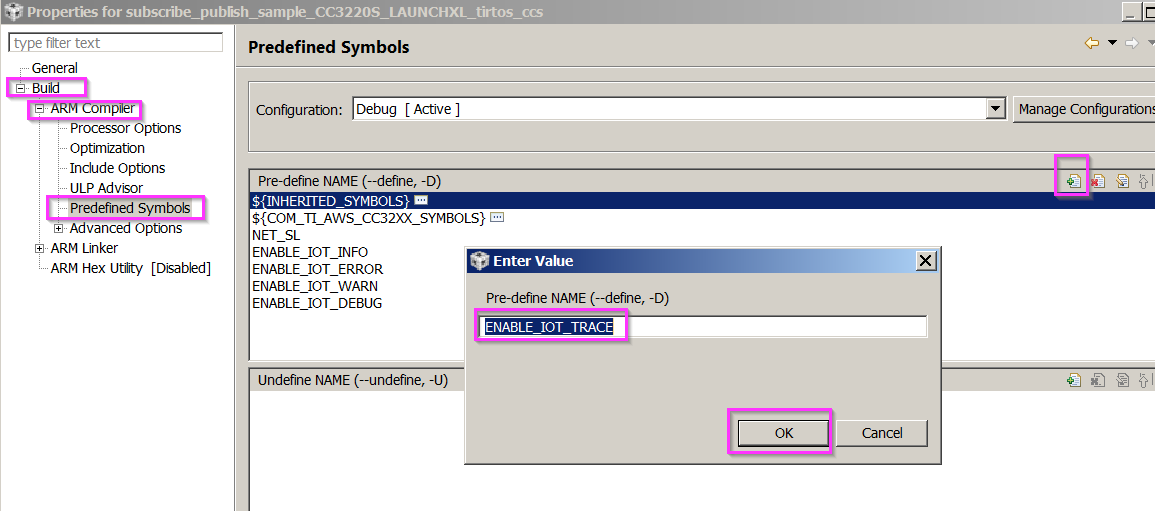
Hi,
I went through the steps described in here
I entered cert names correctly, with "\r\n", as advised in the doc. However the example doesn't work.
Problems:
1. it shows wrong time, startSNTP: Current time is wrong, it's 4 hours ahead than my time zone specified in xxxxxxxxxxxxxxxx.iot.us-east-2.amazonaws.com
2. it fails to connect to xxxxxxxxxxxxxxxx.iot.us-east-2.amazonaws.com
Below is the log:
startSNTP: Current time: Sat Sep 15 14:41:51 2018
CC32XX has connected to AP and acquired an IP address.
IP Address: 192.168.1.13
AWS IoT SDK Version 3.0.1-
Connecting...
ERROR: runAWSClient L#108
Error(-7) connecting to xxxxxxxxxxx.iot.us-east-2.amazonaws.com:8883
Subscribing...
ERROR: runAWSClient L#126
Error subscribing (-13)
ERROR: runAWSClient L#178
An error occurred in the loop. Error code = -13
Can you please advise?
Thanks,
David