Other Parts Discussed in Thread: SHA-256,
Hi,
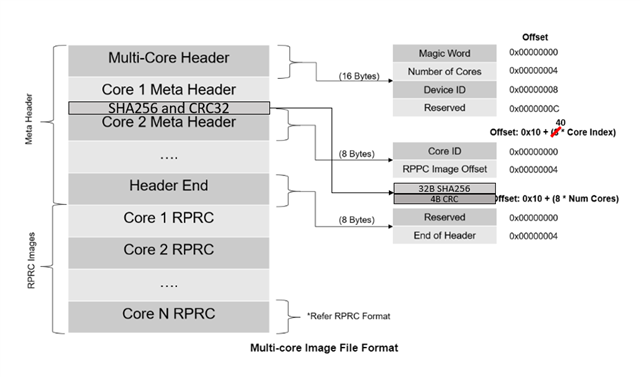
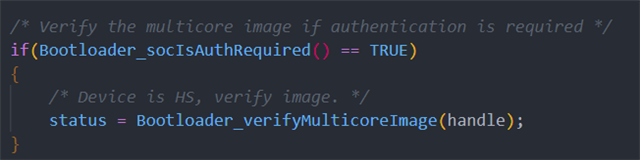
In our application we'd like to calculate and insert SHA-256 and CRC32 data bytes into bootable image binary *.appimage for each core. At which step of bootflow should it be done and how can it be done efficiently?
Thanks,
Wenkai