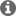Tool/software: Code Composer Studio
This topic is not well documented. I want to password protect my MSP420FR5738 JTAG.
Question 1:
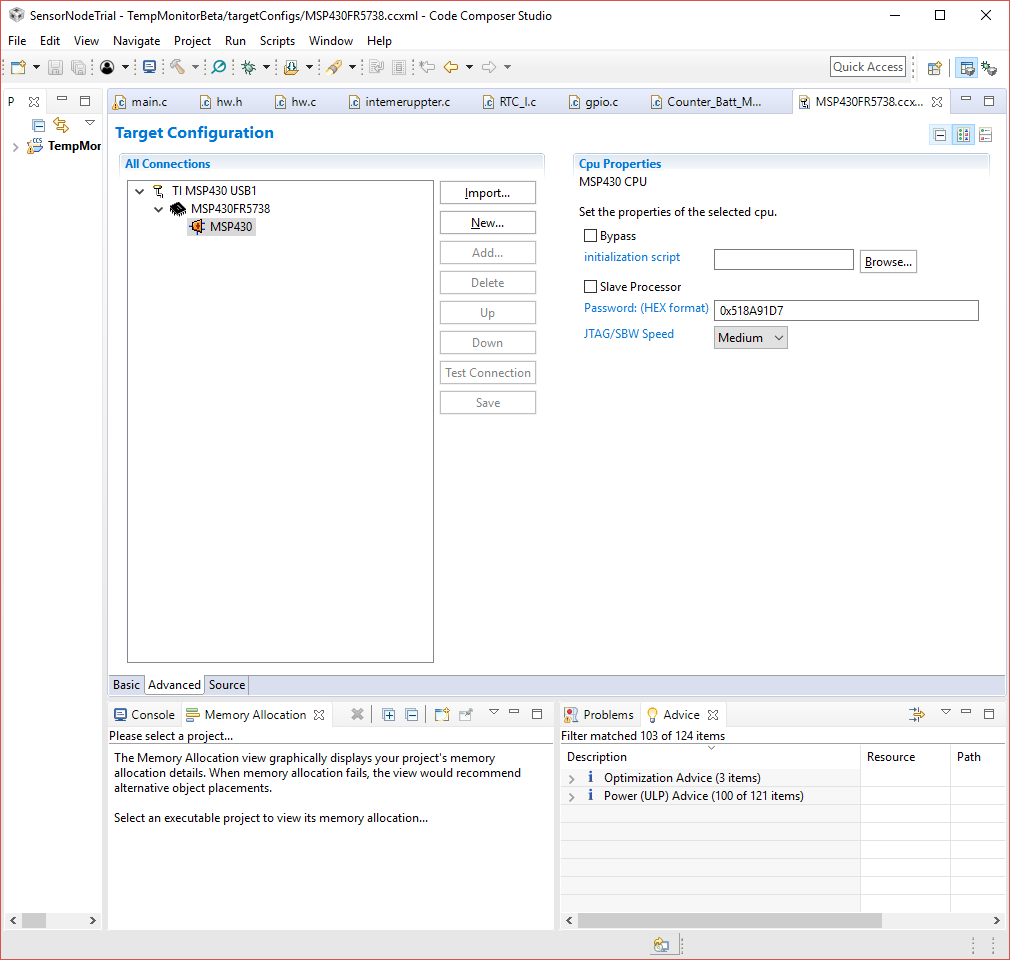
Is it possible to apply a password to the device using MSP Flasher. As far as I can tell, it is NOT possible. Which is very confusing. It's primary use must be as a production programmer, so why would you not have the functionality there? I've tried adding the -p 0xABCD1234 and programmed a few devices (MSP Flasher 1.3.18) . Then I just overwrote them with a different password. It would see that the password is just being ignored.
Question 2:
It doesn't seem to work in CCS either! I've added the following to my code:
#pragma RETAIN(JTAG_signatures)
#pragma DATA_SECTION(JTAG_signatures, ".jtagsignature")
const unsigned short JTAG_signatures[] = {0xAAAA, 0x0002};
#pragma RETAIN(JTAG_password)
#pragma DATA_SECTION(JTAG_password, ".jtagpassword")
const unsigned char JTAG_password[] = {0x8A, 0x51, 0xD7, 0x91};
And then modified the ccxml file accordingly, setting password = 0x518A91D7. Notice the word switheroo required. But every time I try and run up the debugger, it fails :
Error connecting to the target:
The Debug Interface to the device has been secured
For good measure, here's the resulting build from the .txt file:
@ff80
AA AA 02 00 FF FF FF FF 8A 51 D7 91 FF FF FF FF
What's going on!? Does this entire feature just not work? If we think 16 bit, 02 00 => 0002. 8A 51 => 518A. D7 91 => 91D7. Hence my password above.