Other Parts Discussed in Thread: MSP430USBDEVPACK,
Hi,
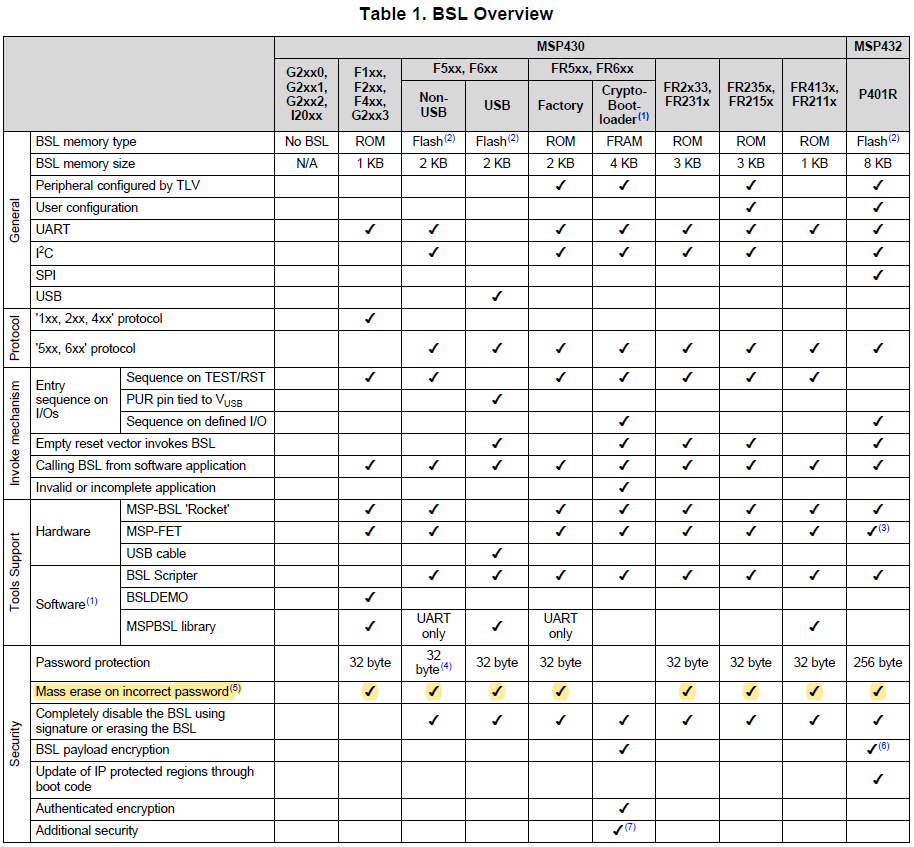
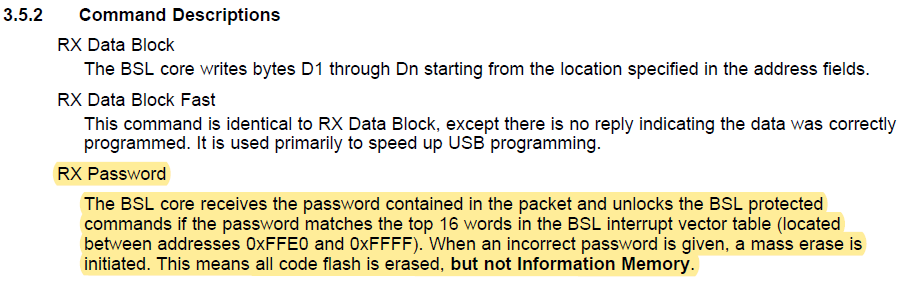
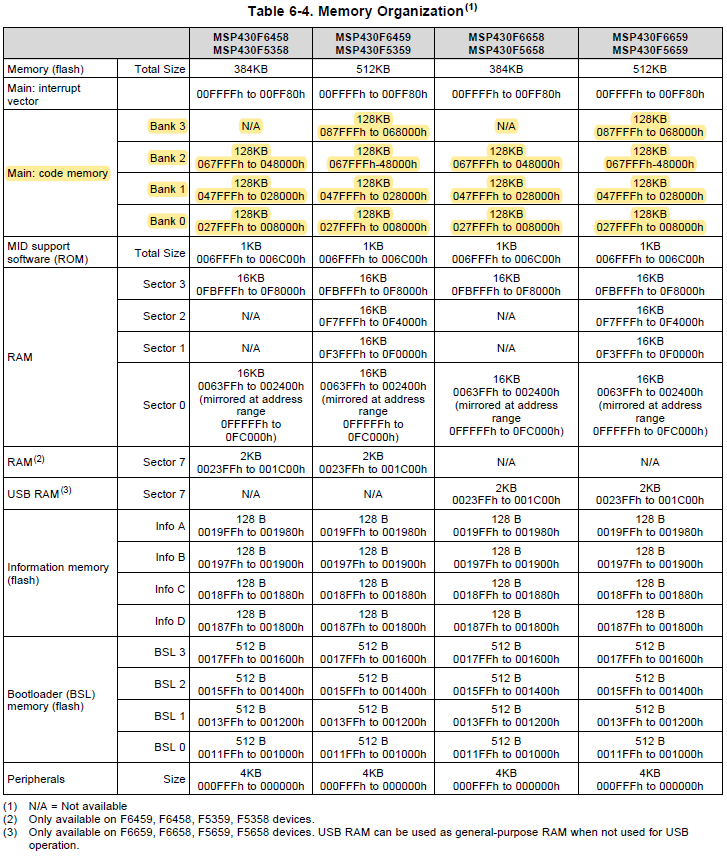
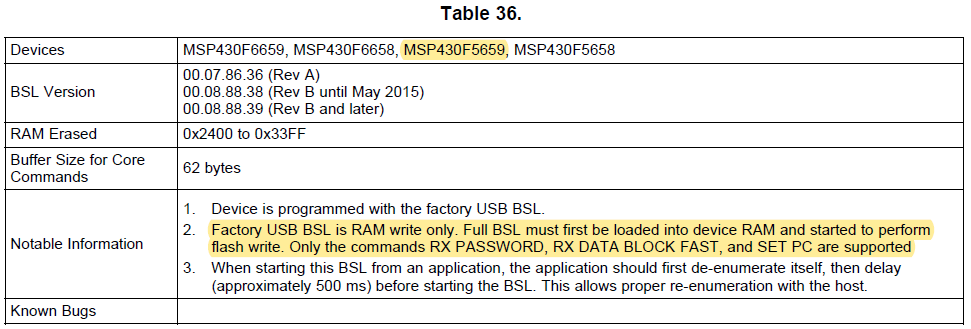
I want to perform a mass erase using the TI USB BSL on my MSP430F5659 via USB. Is there a GUI that exists? I have downloaded MSP430USBDEVPACK, MSP430_USB_Firmware_Upgrade_Example, and BSL scripter, but haven't been able to easily do a mass erase. I think the BSL scripter would do the job, but it looks like I need to write a script. Is there an example or something that exists? Also, from the source code of BSL_USB_GUI, there are references to MASS_ERASE, but the GUI does not have the option of just doing that.
Thank you,
Fred