Other Parts Discussed in Thread: BQSTUDIO, BQ26100, EV2400
Hi, We are using BQ78350-R1 for battery management. For testing purpose, we have connected that module to pc through EV2300.
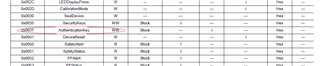
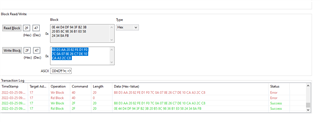
PC side we are using Battery Management Studio ( bqStudio ) 1.3.101. As per our requirement, we have to authenticate the battery as connected to our PCB. So to authenticate, we require default Authentication Key.
Using BQStudio, we are unable to fetch the Authentication key. So we want help, regarding this.
Waiting for your kindly reply
Thanks & Regards
Tapasendra Datta