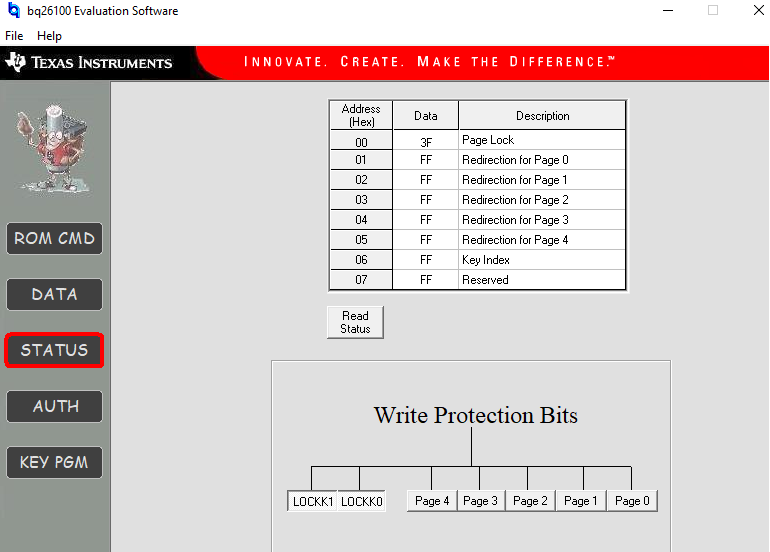
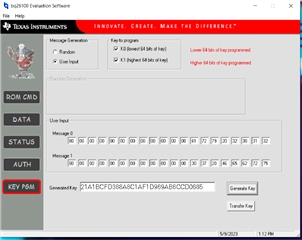
I have the software running and the EV2300 connected to the EVM. I know its a good lash up as I can read the contents of memory using the DATA tab.
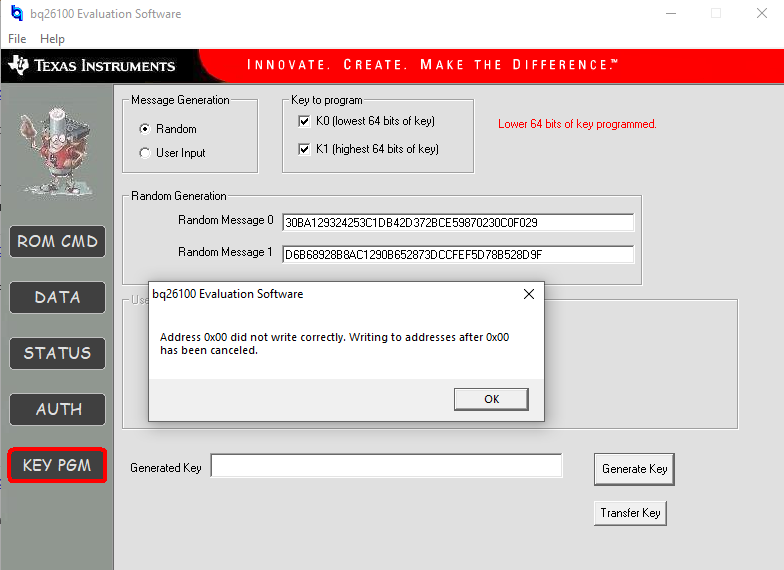
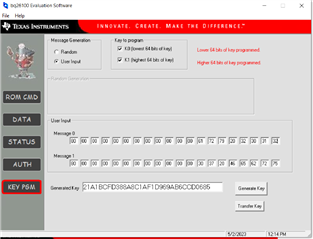
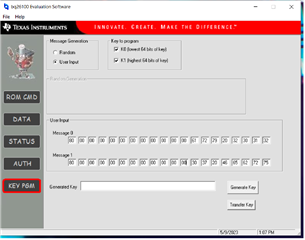
I cannot seem to grasp the operation of the KEYPGM button. I see the Message0 and Message1 boxes that I assume I am to put in my secret key values. I am just not sure where to put them. Way more boxes than required for my 64 bit key. I read the padding explanation but adding a 1 and the number of zeros doesn't add up either. So I chose Random and hit the generate key button to see where that puts the key.. That fills in a key into Message 0. With an error.
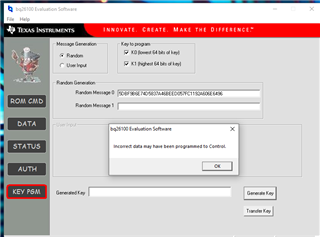
So then using that as guide, I enter a 64 bit key into message 0 and hit Generate Key. That gives an error as well.
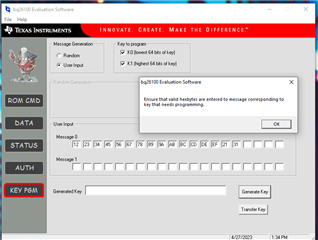
I know I am missing something that should be obvious, but I can't seem to get around it.
Using my Secret Key as above please tell me how to fill in the boxes so that it will store the key.
thanks
dpk