Other Parts Discussed in Thread: CC2541, , CC-DEBUGGER
Hi,
Good Day.
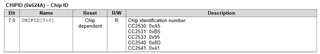
Customer would like to read chip ID on a board connected to a PC by CCDebugger by using the SmartRFProgConsole.exe
He have two different programs: one for a CC2540 and the other for a CC2541 so he want to automatically detect the chip and program it with the right program.
Please advise. Thank you very much.
Best Regards,
Ray Vincent