Other Parts Discussed in Thread: BLE-STACK,
HI,
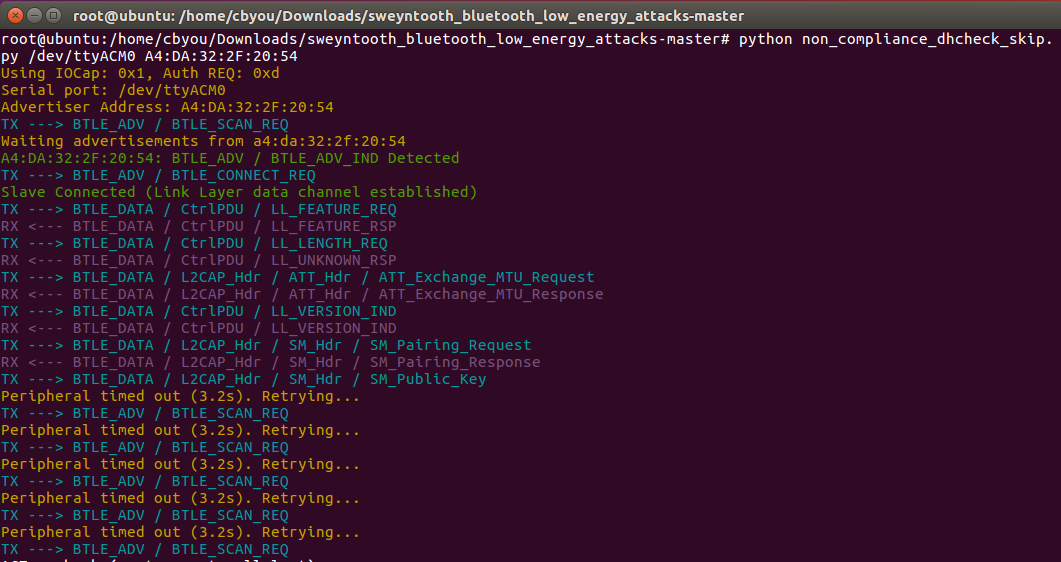
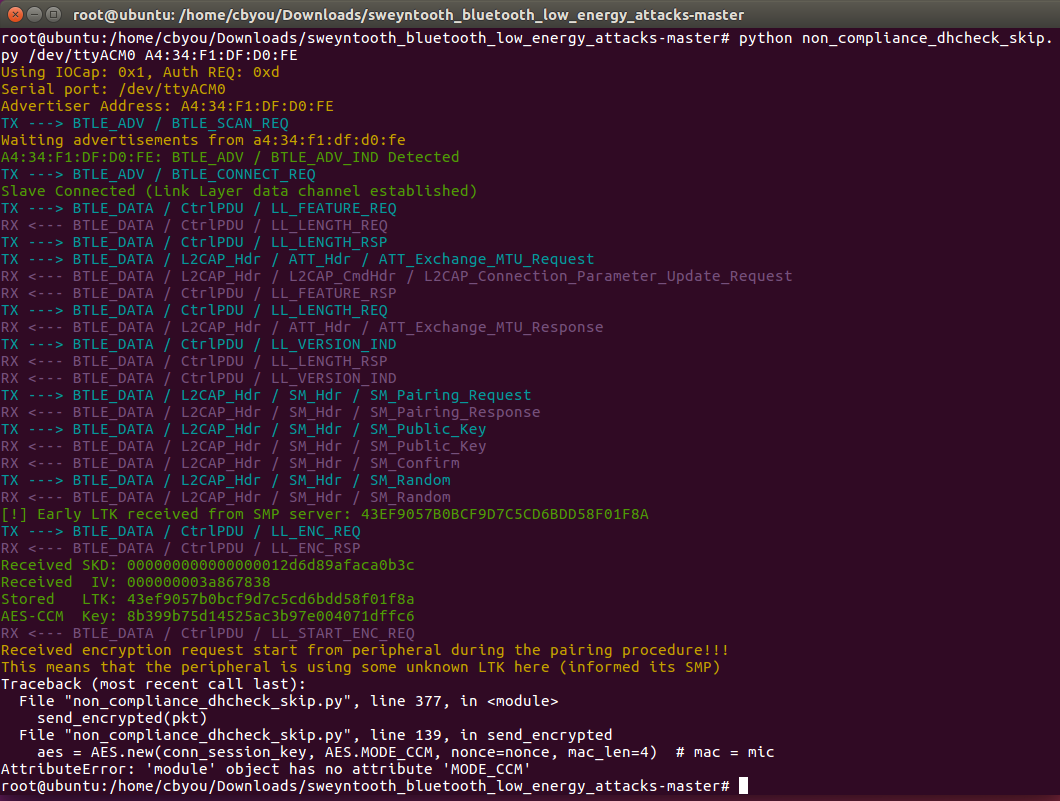
Does CVE-2020-13593 affect BLE-STACK-2-2-4 and CC2640R2 SDK 4.10 ?
or Do these patches below fix the CVE-2020-13593 Vulnerabilities ?
1. Updated the LE Secure Connections pairing process to avoid skipping DHkey check during pairing procedure
2.
|
ID |
Summary |
|
BLESTACK-5310 |
Fixed a specification incompliance where the DH Key check was skipped on the device in the peripheral role if a central device attempted to start encryption before it sends a DH Key check value to the peripheral |