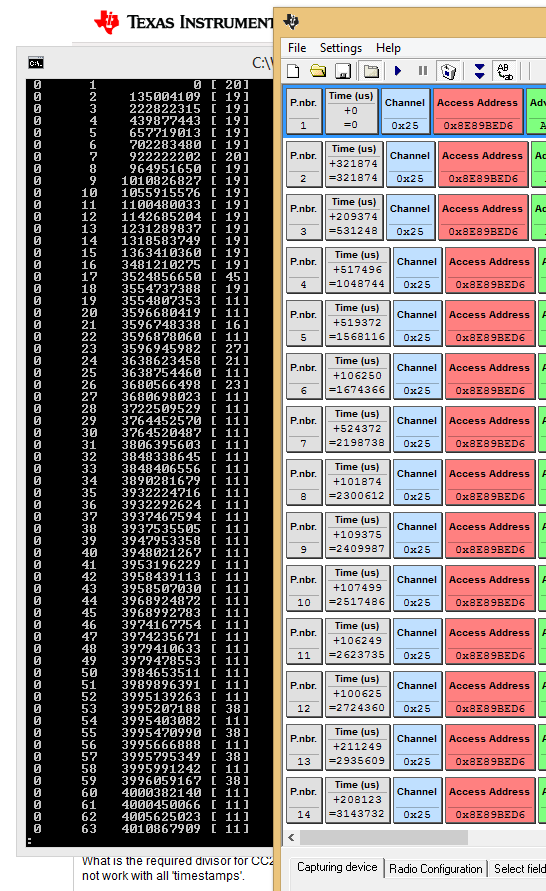
I have read the document about PSD files, but i haven't seen how is stored the information on the BLE channel used by the packet.
I also have a question about the timestamp field (8 octets field), the value in the PSD file should be divided by some clock value to get the time in microseconds. From what i can observe the ratio between the file and the value displayed by the packet snifer is about 419.4
Have I missed some documentation addendum?
Thanks for any pointer
Laurent