Part Number: LAUNCHXL-CC1310
Other Parts Discussed in Thread: CC1310
HI
I have some questions.
Examples code: rfwsnNode and rfwsnconcentrator
sdk: simplelink_cc13x0_sdk_1_50_00_08
Used board: cc1310 LP
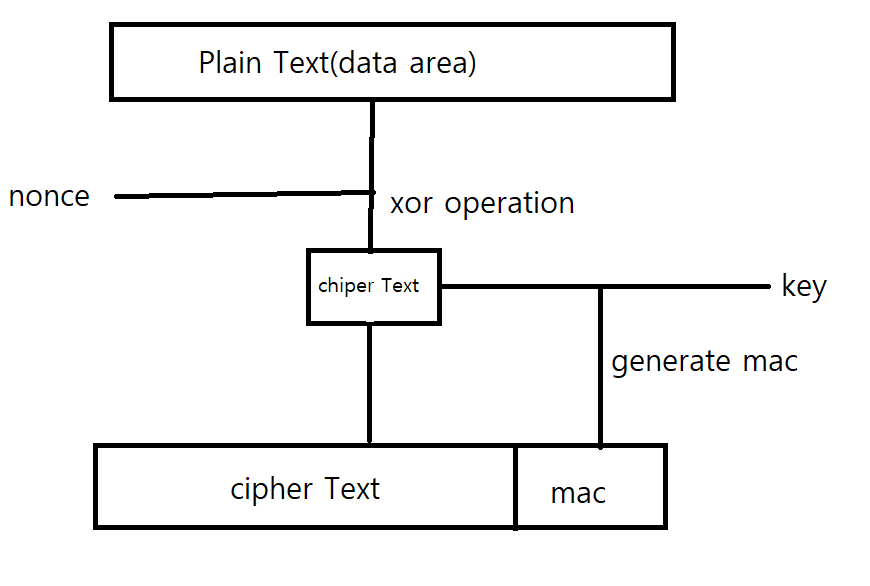
I would like to apply Encryption to the example code above. And I also found that there is CryptoCC26XX.h.
1.Do you have any examples for encryption / decryption?
(I would like to exclude things like ECB, because it is not recommanded.)
2.If there is an encryption / decryption example, can the following packet also apply?
(The packet frame structure is based on easylink.)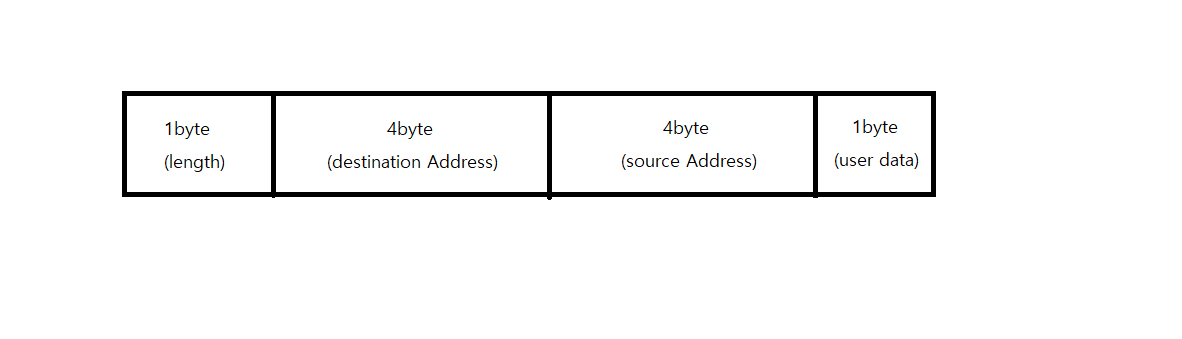
Thanks.