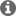Other Parts Discussed in Thread: CC1352P, CC1350, UNIFLASH, LAUNCHXL-CC1350, CC1310, CC1312R, LAUNCHXL-CC1312R1, , , LAUNCHXL-CC1352P1, LAUNCHXL-CC1310
Tool/software: TI-RTOS
Hi all,
i am using CC1352P _ FH mode- Collector - sensor
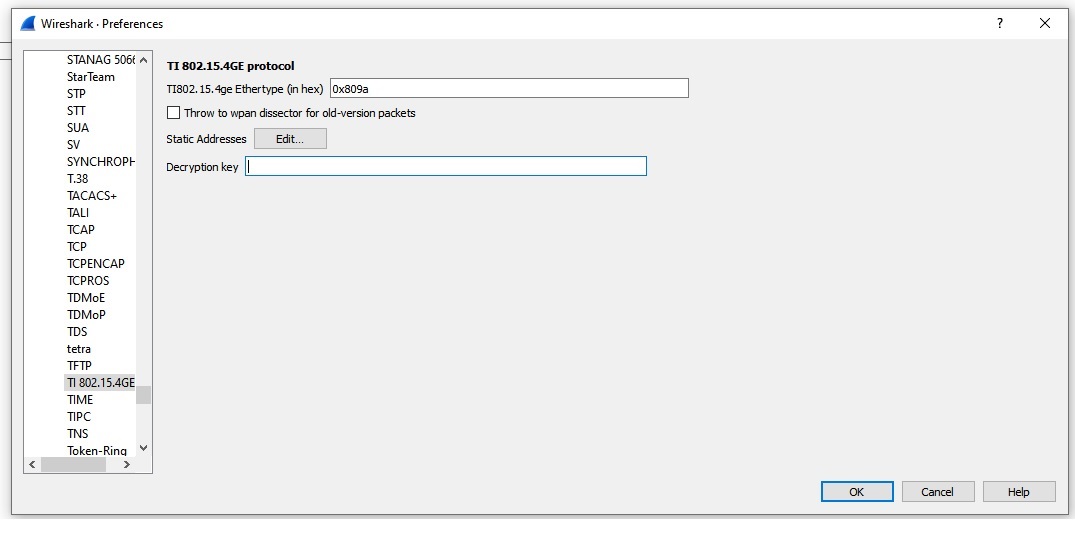
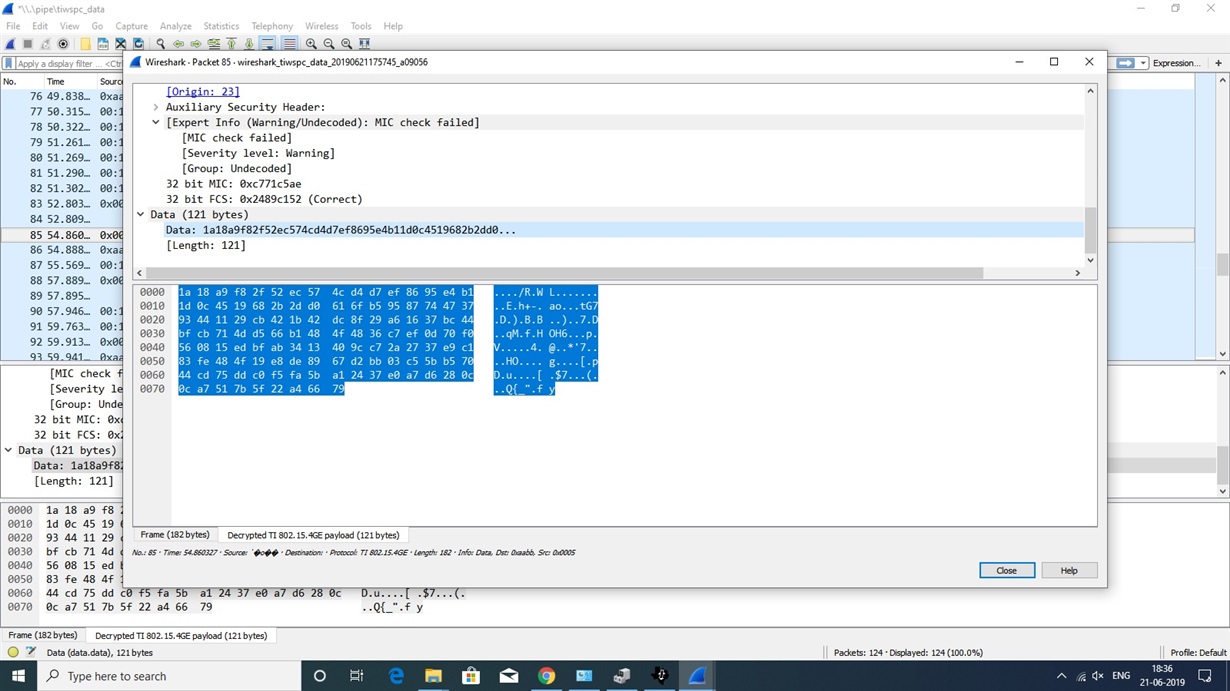
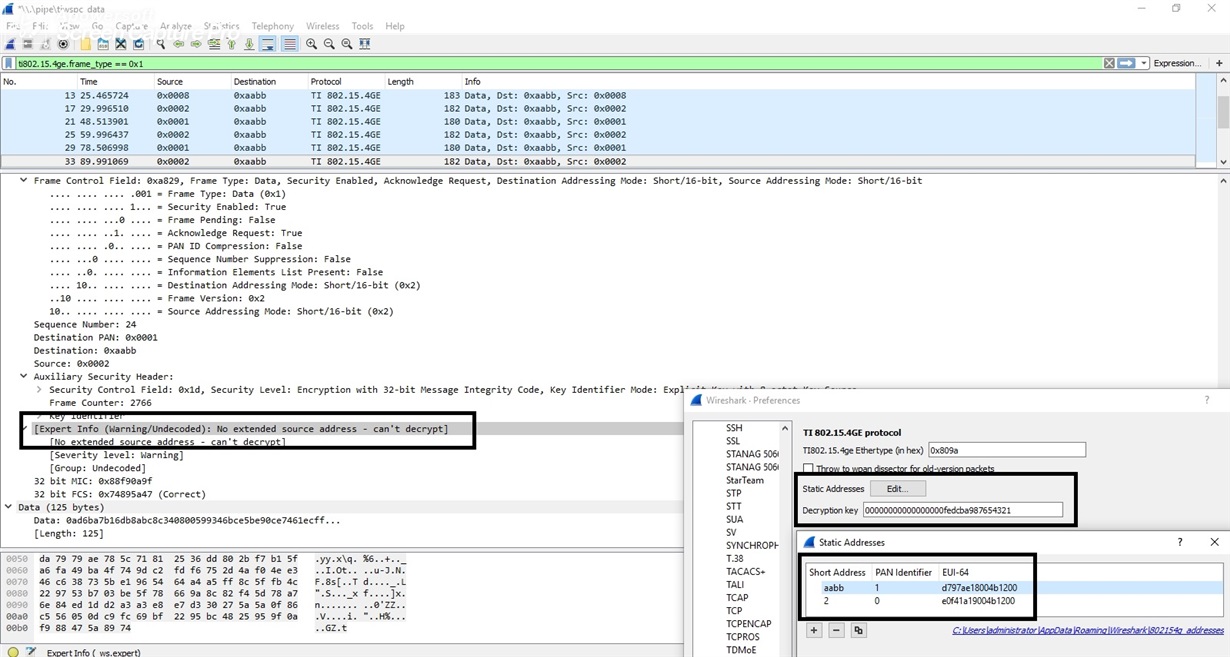
i want to remove the security in the both side and do the communication and after that i have to see the data in the packetr sniffer,
because now security is enable and i can see the encrypted data but i can't see the actual data. so i need ot disable security and then i can check the details in the packet sniffer.
Anil.