Other Parts Discussed in Thread: UNIFLASH
Hi,
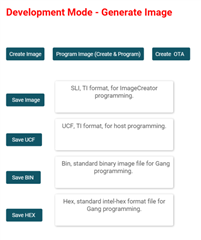
we've hit yet another badly documented and somewhat broken "feature" in the Uniflash/Gangimage process. We're trying to build a Gangimage with an mcu image signed with a certificate (not with the dummy-root-ca).
I've created an empty gang image project, changed the trusted root catalog to certcatalog20200715.lst with the signature in certcatalog20200715.lst.signed_323x.bin.
From the documentation:
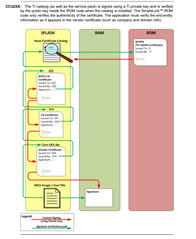
The signed certificates filename should be created in the device with the name as it appears under the “issued to” property of the certificate (the exact name should be given).
I expected to have to add the DER encoded signing certificate as file to the gang image with the value of the Common Name certificate attribute as the file. So, if the common name of the certificate is My Signing Certificate, i would add the certificate with the exact filename. However, Uniflash automatically changes the filename to lowercase (not really sure if that matters).
Then I've added our mcuimg.bin with the signature signed by the certificate (i've verified it via openssl that the signature is indeed correct). However, when flashing the gang image, i get the error -10341 (SL_ERROR_FS_FILE_NOT_EXISTS). From what I've gathered from other forum posts, this indicates that the signing certificate could not be found.
So, what is the correct format to add the signing certificate? The documentation conveniently always uses the dummy certificate whose Common Name is lowercase and without spaces.