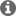Other Parts Discussed in Thread: CC3200, UNIFLASH
We are developing a product with the CC3220MODA SF. And I am trying to understand the PKI technology and vocabulary which is all new to me.
We are not trying to use secure sockets. We are not trying to use secure HTTPS.
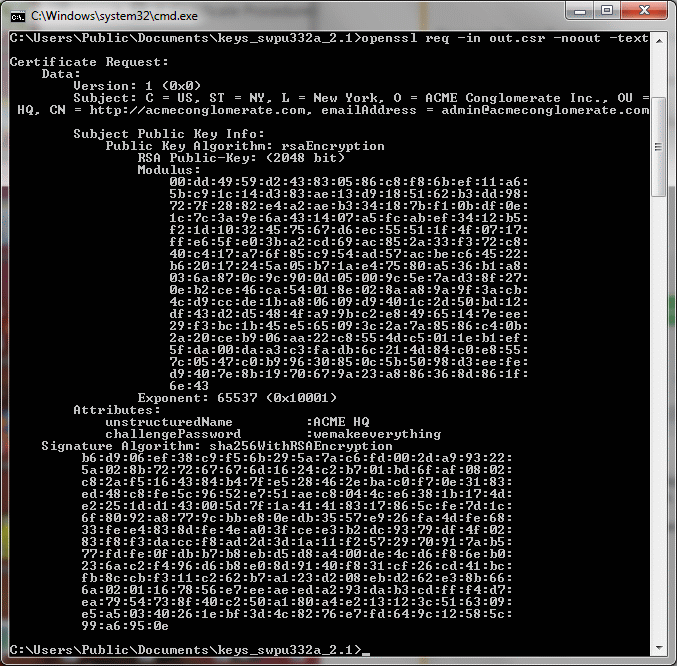
We do not want to pay for a CA to sign our firmware so I think I have determined that I need to learn how to make a self signed certificate catalog and both private key and public key to sign our firmware to be loaded into the CC3220MODA.
On page 170 of SWRU368B is one of many sources of my confusion. The document referees to generation of public keys in for example the Apendix C title which is: How to Generate Certificates, Public Keys, and CAs
However the rest of this appendix only covers generation of a private key and not a key pair which makes me think I am badly misunderstanding something because generating a private key alone would have no value because you could never open a document locked with out the associated public key.
Yet the document, if correct, it goes on to do just that
To create a new private key for a certificate, use:
openssl genrsa -out privkey.pem 2048
And the openssl documentation for genrsa also says it generated a private key and not a key pair.
I see no mention of generating or using a public key. Don't we always need both?
Would like some help understanding the requirements and the PKI vocabulary and OpenSSL implementation then I am hoping to better see the process.
Thanks,
<edited>