Other Parts Discussed in Thread: UNIFLASH, CC3220SF
I am confused by section 6.7.1 of the document SWRU496e.pdf.
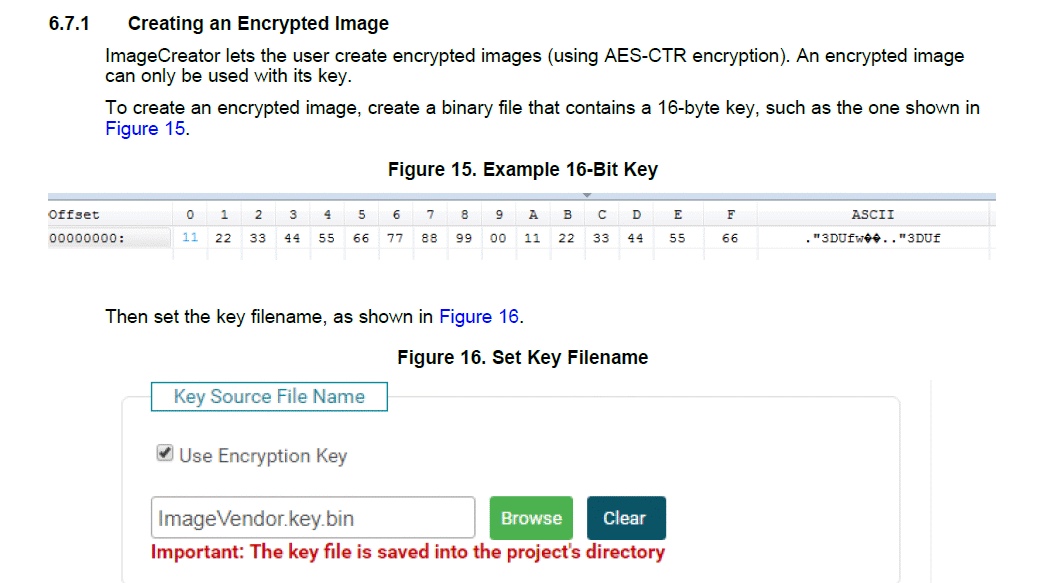
Should not this document be telling us to use either the private key or the public key (I am still trying to figure this out) of a PKI key set which we make with something like OpenSSL key generation?
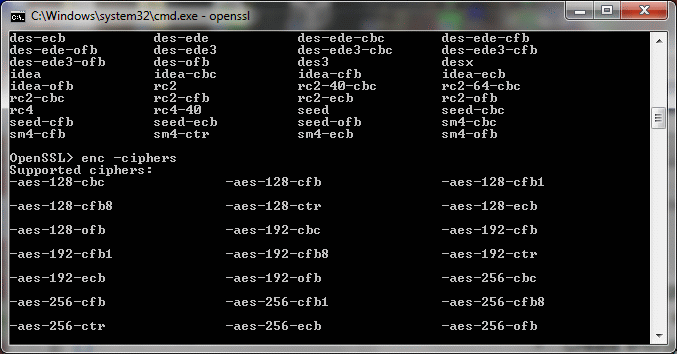
Also could the reference to AES-CTR encryption be one or any of the ciphers beginning with "-aes" returned from the OpenSSL "enc -ciphers" command which I provide here?
If so, should not this document on UniFlash be very specific about the allowed cipher types for keys use with UniFlash and the CC3220SF?
As I say I am struggling with this document and have more questions but this is a start.