Other Parts Discussed in Thread: CC3235SF, UNIFLASH
Hi,
We have been integrating Enterprise Security connection using authentication method EAP-TLS with different networks successfully. However, we are experiencing issues with the latest integration. We are using the SDK version 3.40.00.05 and Service Pack version sp_4.4.1.3_3.1.0.5_3.1.0.19.
According to User's Guide Section 4.6.2 Enterprise Security, the device needs 3 files for EAP-TLS connection:
- Server Root CA file saved under "sys/cert/ca.der" in DER (Binary) or PEM (ASCII) format.
- Client certificate saved under "sys/cert/client.der" in DER (Binary) or PEM (ASCII) format.
- Private key saved under "sys/cert/private.key" in DER (Binary) or PEM (ASCII) format.
In order to prepare the device for authentication, we are given a .pfx file with all necessary certificates which is password protected. Using this given password we also use openssl commands to convert them into supported format of TI. The openssl command that we have been using is "openssl.exe pkcs12 -in certificates.pfx -out certificates.cer -nodes". This command asks for the password and puts all certificates in PEM (ASCII) format in one file. Later, each part with the corresponding "-----BEGIN *** -----END ***" texts have been copied to separate files with certain names given above.
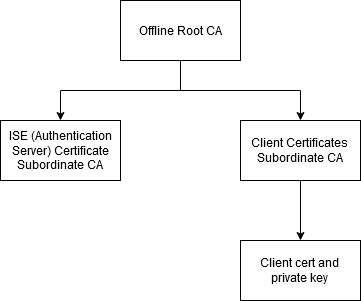
This has been working for many different integrations but the latest Enterprise Security integration has a different topology of CA than the others. Until now, we were given one Root CA and one client certificate with one private key where the client certificate was issued by the Root CA. The latest integration has one offline Root CA which has issued two different subordinate CAs. The first subordinate CA is the ISE (Authentication Server) Certificate and the second subordinate CA is the issuer of all client certificates (I'm calling this Client Subordinate CA from now on). So the topology for each CA and client certificate is like this:
- Offline Root CA
- ISE (Authentication Server) Certificate Subordinate CA
- Offline Root CA
- Client Subordinate CA
- Client Certificate and Private Key
- Client Subordinate CA
I would like to understand which of these CAs will help me connect successfully to the network. We first tried connecting to the network with Offline Root CA as the file number 1 ("sys/cert/ca.der"). Later, we tried ISE (Authentication Server) Certificate Subordinate CA and Client Subordinate CA as the file number 1 ("sys/cert/ca.der") but no success.
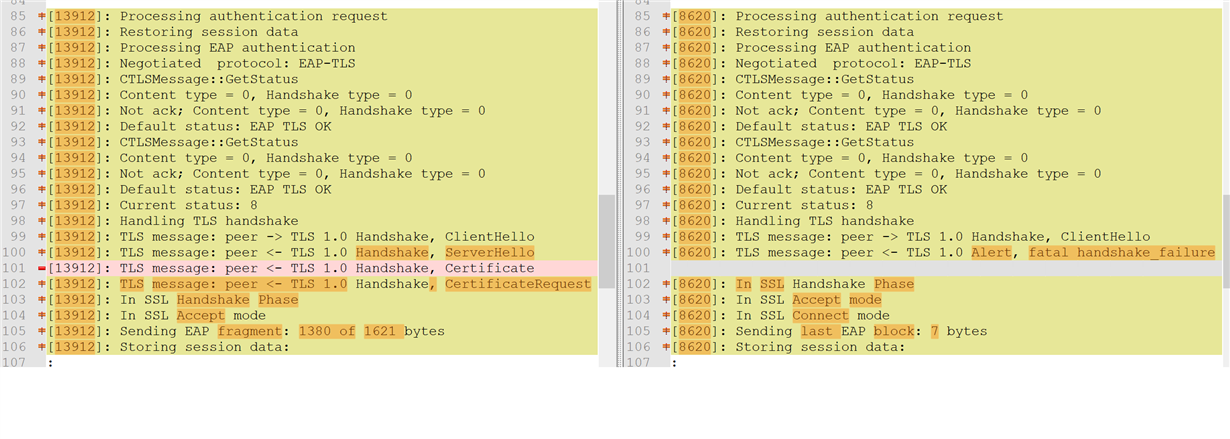
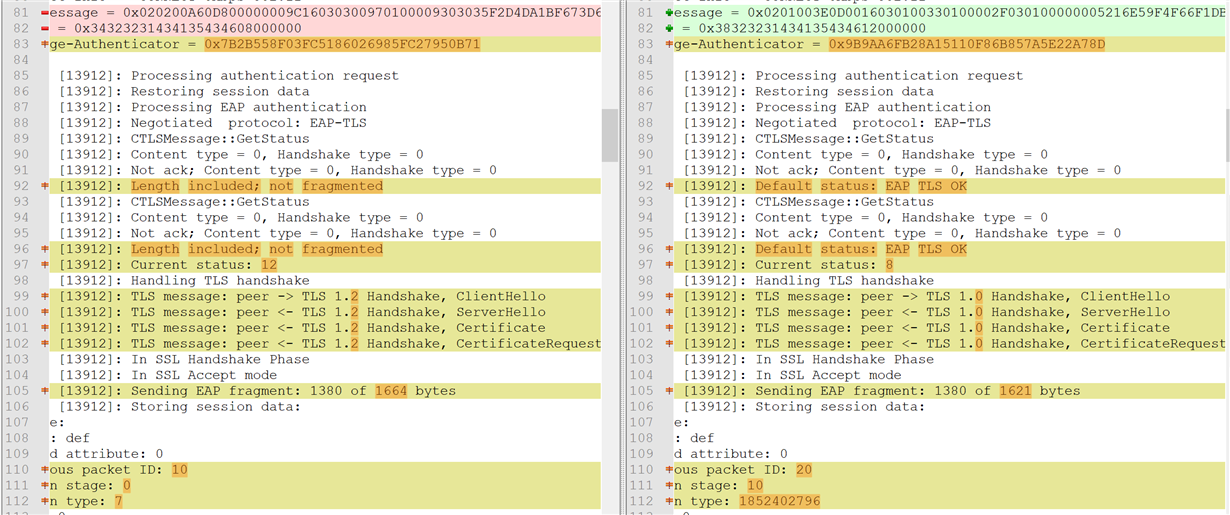
Looking at the logs from the device, the connection to the AP is successful with SL_WLAN_EVENT_CONNECT and the WPA2 Enterprise connection request with EAP-TLS is sent. However, the device receives a SL_WLAN_EVENT_DISCONNECT event with the reason code 2 SL_WLAN_DISCONNECT_AUTH_NO_LONGER_VALID right after. We have tried initiating the connection with adding a profile and enabling auto connection, as well as using sl_WlanConnect function, but the results are the same. Lastly, we have tried to disable server authentication using the code below but the connection still fails after these trials.
/* Disable server authentication. */ _u8 param = 0; /* 0 means disable the server authentication */ slRet = sl_WlanSet(SL_WLAN_CFG_GENERAL_PARAM_ID, \ SL_WLAN_GENERAL_PARAM_DISABLE_ENT_SERVER_AUTH, \ 1, ¶m);
Looking at the logs from the Radius Server there are several different reasons for the failure. It can be seen that the EAP-TLS request reaches the Radius Server and the Radius Server responds but something goes wrong on the next steps. Several reasons are given below:
| Event | Failure Reason | Resolution | Root cause |
| 5400 | 12520 EAP-TLS failed SSL/TLS handshake because the client rejected the ISE local-certificate | Check whether the proper server certificate is installed and configured for EAP in the Local Certificates page ( Administration > System > Certificates > Local Certificates ). Also ensure that the certificate authority that signed this server certificate is correctly installed in client's supplicant. Check the previous steps in the log for this EAP-TLS conversation for a message indicating why the handshake failed. Check the OpenSSLErrorMessage and OpenSSLErrorStack for more information. | EAP-TLS failed SSL/TLS handshake because the client rejected the ISE local-certificate |
| 5440 | 5440 Endpoint abandoned EAP session and started new | Verify known NAD or supplicant issues and published bugs. Verify NAD and supplicant configuration. | Endpoint started new authentication while previous is still in progress. Most probable that supplicant on that endpoint stopped conducting the previous authentication and started the new one. Closing the previous authentication. |
| 5411 | 12935 Supplicant stopped responding to ISE during EAP-TLS certificate exchange | Verify that supplicant is configured properly to conduct a full EAP conversation with ISE. Verify that NAS is configured properly to transfer EAP messages to/from supplicant. Verify that supplicant or NAS does not have a short timeout for EAP conversation. Check the network that connects the Network Access Server to ISE.Verify that ISE local server certificate is trusted on supplicant. Verify that supplicant has a properly configured user/machine certificate. | Supplicant stopped responding to ISE during EAP-TLS certificate exchange |
Looking at the logs from the Wireshark captures, we are seeing de-authentication packet coming from our TI device to the AP. The conversation between the server and client through the AP is given below:
| Time | Source | Destination | Protocol | Info | SN | FN |
| 6.156844 | TexasIns | Broadcast | 802.11 | Probe Request | 0 | 0 |
| 6.157468 | AP | TexasIns | 802.11 | Probe Response | 623 | 0 |
| 6.163295 | TexasIns | Broadcast | 802.11 | Probe Request | 1 | 0 |
| 6.163768 | AP | TexasIns | 802.11 | Probe Response | 624 | 0 |
| 6.261852 | TexasIns | AP | 802.11 | Deauthentication | 0 | 0 |
| 6.262140 | TexasIns | AP | 802.11 | Authentication | 1 | 0 |
| 6.263200 | AP | TexasIns | 802.11 | Authentication | 256 | 0 |
| 6.264223 | TexasIns | AP | 802.11 | Association Request | 2 | 0 |
| 6.265788 | AP | TexasIns | 802.11 | Association Response | 256 | 0 |
| 6.275755 | AP | TexasIns | EAP | Request Identity | ||
| 6.276947 | TexasIns | AP | EAP | Response Identity | ||
| 6.284551 | AP | TexasIns | EAP | Request, TLS EAP | ||
| 6.303176 | TexasIns | AP | TLSv1 | Client Hello | ||
| 6.326566 | AP | TexasIns | EAP | Request, TLS EAP | ||
| 6.327411 | TexasIns | AP | EAP | Response, TLS EAP | ||
| 6.340577 | AP | TexasIns | EAP | Request, TLS EAP | ||
| 6.342613 | TexasIns | AP | EAP | Response, TLS EAP | ||
| 6.355674 | AP | TexasIns | EAP | Request, TLS EAP | ||
| 6.357706 | TexasIns | AP | EAP | Response, TLS EAP | ||
| 6.372640 | AP | TexasIns | EAP | Request, TLS EAP | ||
| 6.374426 | TexasIns | AP | EAP | Response, TLS EAP | ||
| 6.389659 | AP | TexasIns | EAP | Request, TLS EAP | ||
| 6.391666 | TexasIns | AP | EAP | Response, TLS EAP | ||
| 6.401470 | AP | TexasIns | TLSv1 | Server Hello, Certificate, Certificate Request, Server Hello Done |
Please help me understand the reason behind these failures and tell me which configuration I am doing wrong or missing.
Also, if you need more information at any point please let me know.
Best,