Other Parts Discussed in Thread: UNIFLASH
Hi All,
I am using TI RTOS and CCS6 with tm4c129encpdt and xdc tools 3.32 with cc3100
I am using httpcli library for https and MQTT.
I am creating an MQTT client and able to send and receive messages. Also, I am able to do https using the same. I am using TLS for both using httpcli library which uses simplelink stack inside it.
What I am doing is-
I have created TLS for HTTP once and using it throughout the program until reset. And for MQTT, I am creating TLS, connecting to the MQTT server, sending messages, and then closing it. Due to this reason, I am creating each time a new TLS and deleting it also with this code-
Create TLS for https-
TLS_Params tlsParams;
TLS_Params_init(&tlsParams);
tlsParams.ca = ca_cert;
tlsParams.calen = sizeof_ca_cert;
g_tls = TLS_create(TLS_METHOD_CLIENT_TLSV1_2, &tlsParams, NULL); //g_tls is a global variable
if (!g_tls) {
logg("***ERROR*** - TLS_create failed",__FUNCTION__);
ret=-1;returnVal = false;goto cleanup;
}
Delete TLS for HTTPS-
TLS_delete(&g_tls);
g_tls = NULL;
Create TLS for MQTT-
TLS_Params_init(&aws_tlsPar);
aws_tlsPar.ca = pRootCALocation ; // certs to be done later akhilesh
aws_tlsPar.calen = root_ca_pem_len;//
aws_tlsPar.cert = pDeviceCertLocation;
aws_tlsPar.certlen = strlen(pDeviceCertLocation);//cert_pem_len;//client_cert_pem_len;//
aws_tlsPar.key = pDevicePrivateKeyLocation;
aws_tlsPar.keylen = strlen(pDevicePrivateKeyLocation);//private_key_pem_len;//>pDevicePrivateKeyLocation);
aws_tls = TLS_create(TLS_METHOD_CLIENT_TLSV1_2, &aws_tlsPar, NULL);
if (!aws_tls) {
ret = FAILURE;
goto QUIT;
}
Delete tls for MQTT-
TLS_delete(&aws_tls);
tlsDataParams->aws_tls = NULL;
Now the issue is-
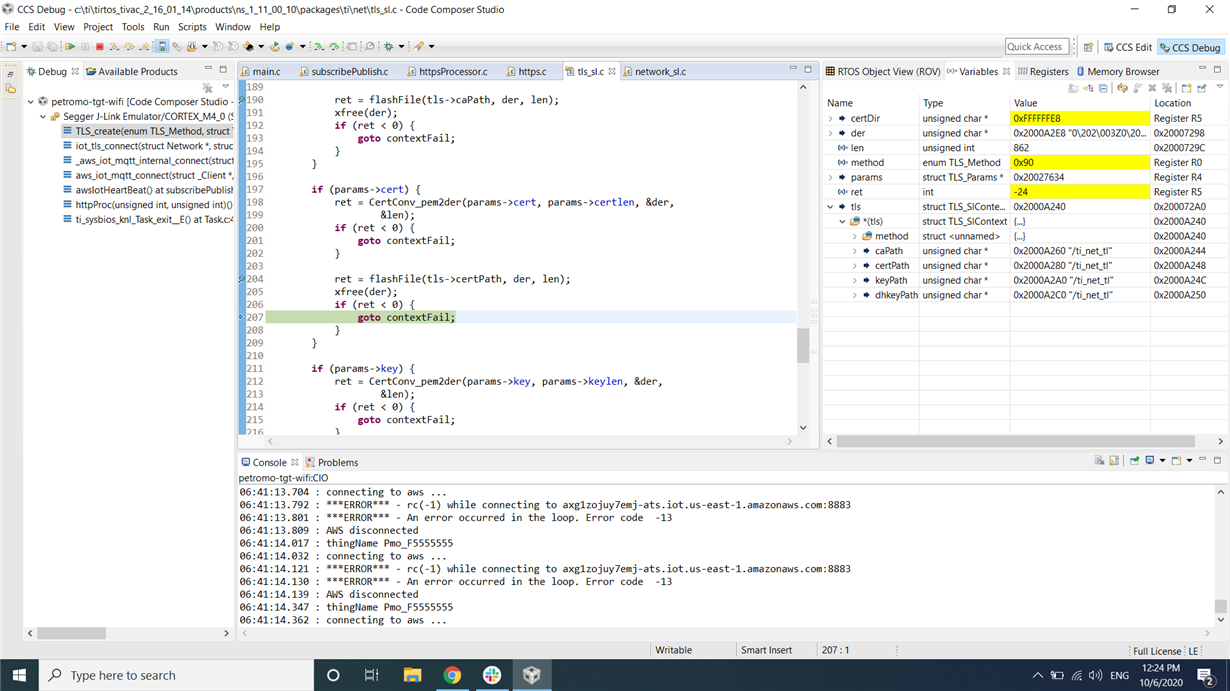
This works only for a certain no of times and later on when I do MQTT multiple times, my TLS getting failed. I debugged a bit more and found out that after some certain no of times, inside the TLS_create function in the file tls_sl.c, line no 204,
if (params->cert) {
ret = CertConv_pem2der(params->cert, params->certlen, &der,
&len);
if (ret < 0) {
goto contextFail;
}
ret = flashFile(tls->certPath, der, len); ///////////// here getting -24
xfree(der);
if (ret < 0) {
goto contextFail;
}
I am attaching the screenshot also. this flashFile is returning the -24 while burning certificate and private key only. For root ca is works fine. I checked the parameters are fine. Also, this issue comes when I create TLS multiple times after deleting them.
The path for cert file was - /ti_net_tls11.cert. This was the path I checked. Please let me know. This TLS issue I am facing in ethernet also. Even though I delete the TLS, but each time when I create the new TLS, it is getting a new path directory and it increases each time by one.
Just for sharing, I have ported AWS MQTT Client SDK into my project and I interfaced it with httpcli library so that I can use the same code of MQTT into ethernet and wifi. But This TLS issue is coming.
Let me know. I am stuck here.
Thanks
Akhi