Other Parts Discussed in Thread: Z-STACK, CC2530
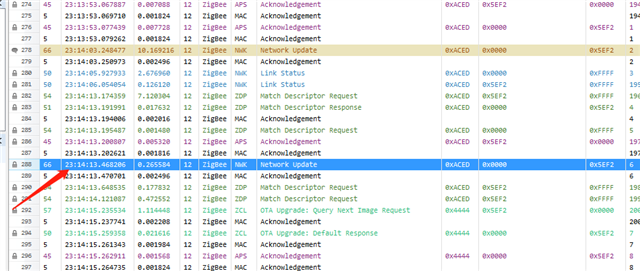
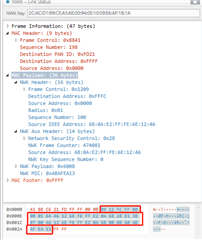
My customer is testing a zigbee network with CC2652P as end devices to comminucate with a Silabs coordinator. They found that the coordinator does not increment the nwkUpdateId field when sending the UPDATE PANID REQ, therefore the request will be dumped by CC2652 and the new PANID is not accepted.
Is there a workaround to make CC2652P accpet the UPDATE PANID REQ without increment of nwkUpdateId?
Best regards,
Shuyang