Other Parts Discussed in Thread: Z-STACK
Z-Stack Linux server "as is" does not support unsecure rejoin which is fine for us. However, we have some quite old plugs with acting as a router in the field which do allow unsecure rejoin.
What happens is that the plug (56C1) will let an end-device (CADF) rejoin insecurely and it will then notify the coordinator:
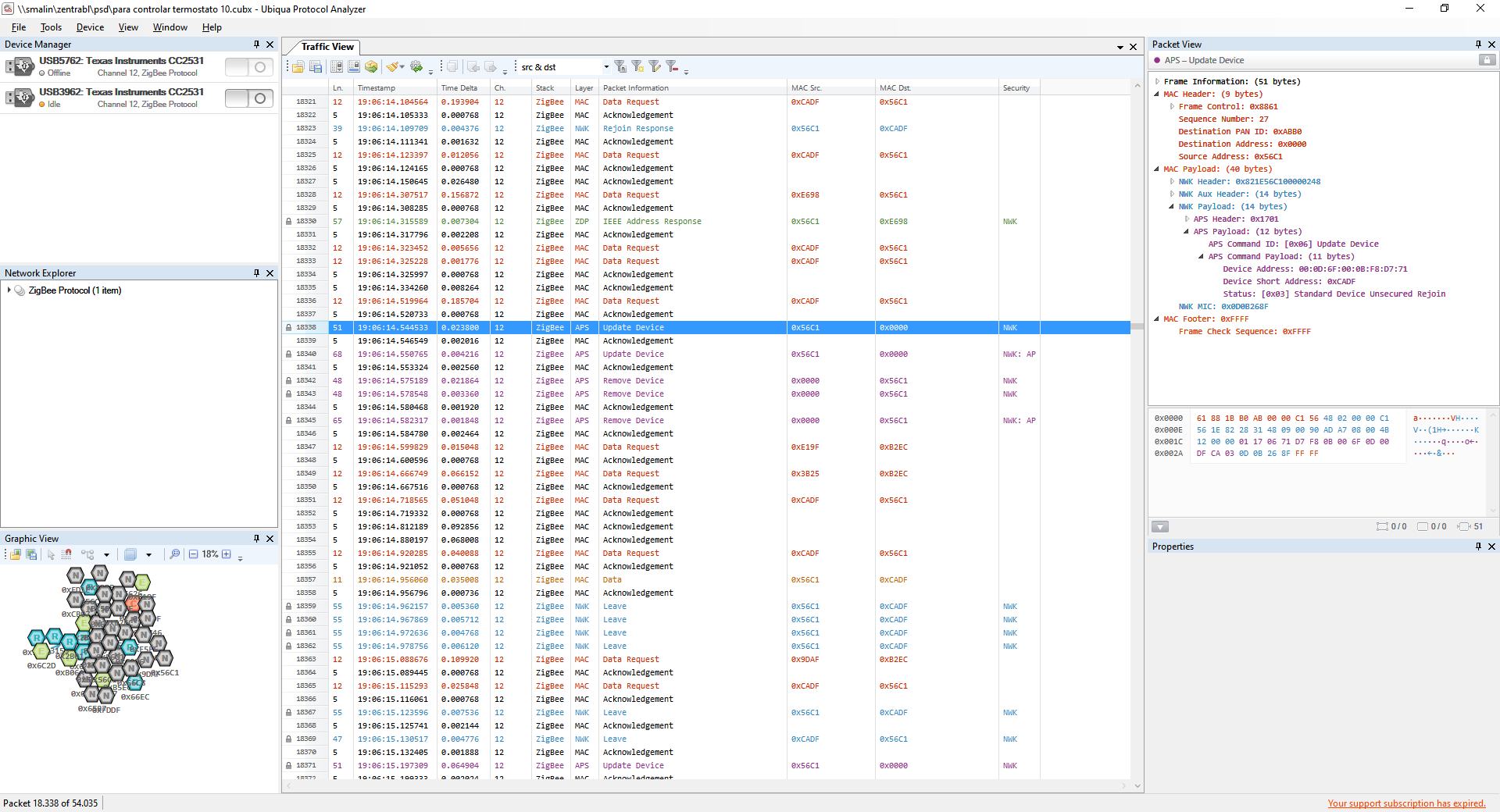
The coordinator will then send a Remove Device message and the end-device gets lost.
Is there any way to configure the coordinator in a way that itself will not process unsecure rejoins but tolerate Update Device messages from routers even if the end-device has rejoins insecurely?
Regards
Peter

