Other Parts Discussed in Thread: CC3220SF, UNIFLASH
Tool/software: TI-RTOS
Hi All,
Recently, I program AWS SDK (aws_cc3220_1_10_00_07) to CC3220SF LaunchPad to connect to AWS IoT
I followed this thread (e2e.ti.com/.../593513 to set up
my setting:
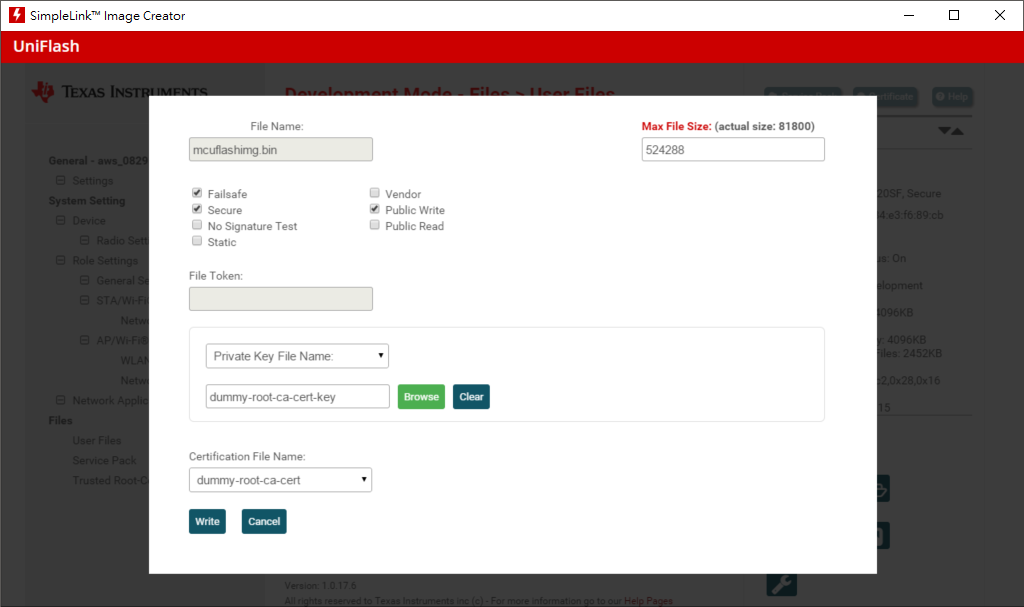
Step 1. Select MCU Image add subscribe_publish_sample_CC3220SF_LAUNCHXL_tirtos_ccs.bin (mcuflashimg.bin)
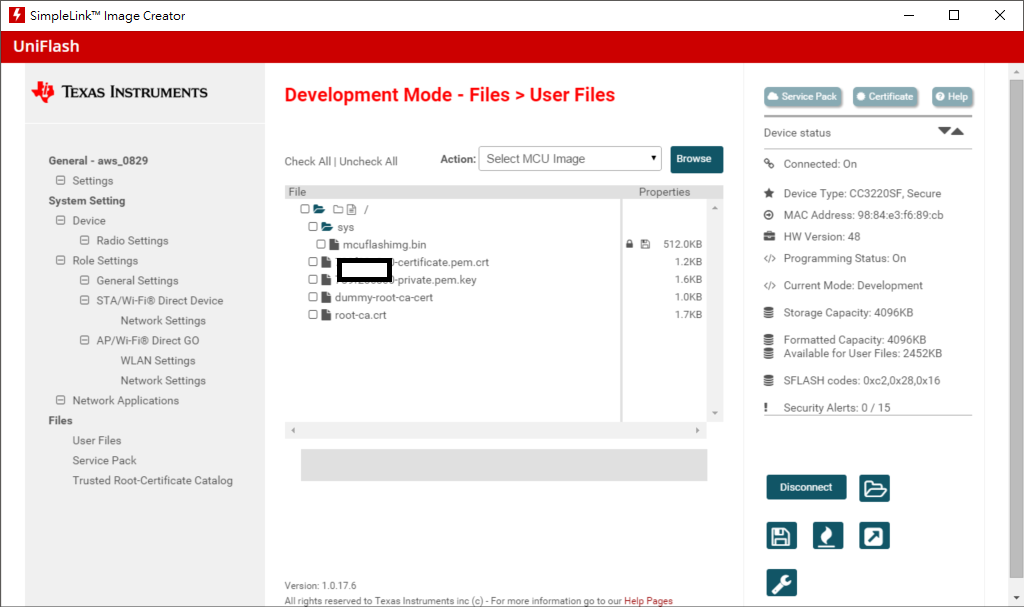
Step2. add file for TLS Protocol ( root-ca, certificate, private key ) and subscribe_publish_sample_CC3220SF_LAUNCHXL_tirtos_ccs.bin
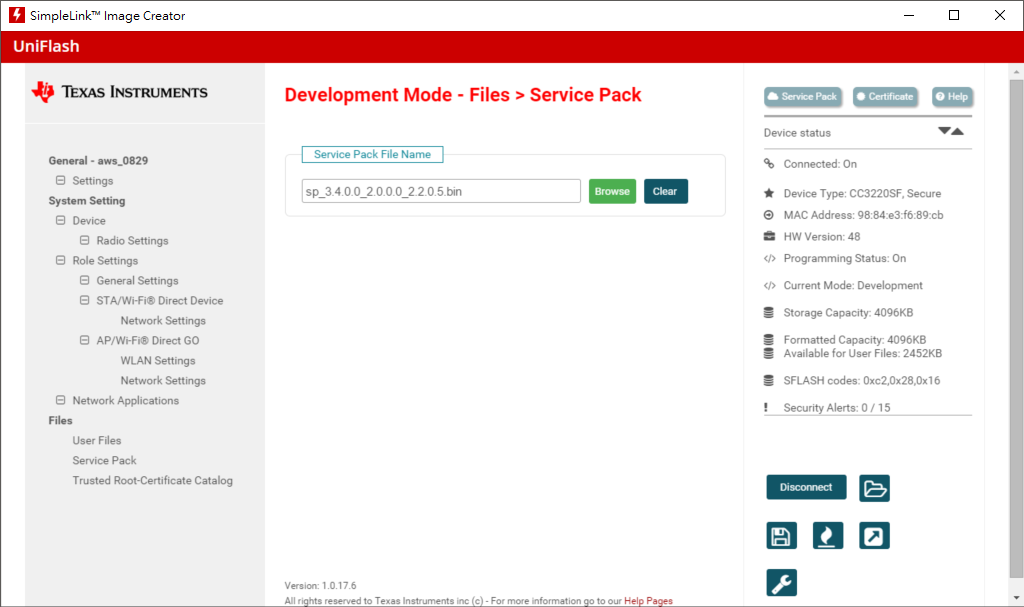
Step3. add Service Pack
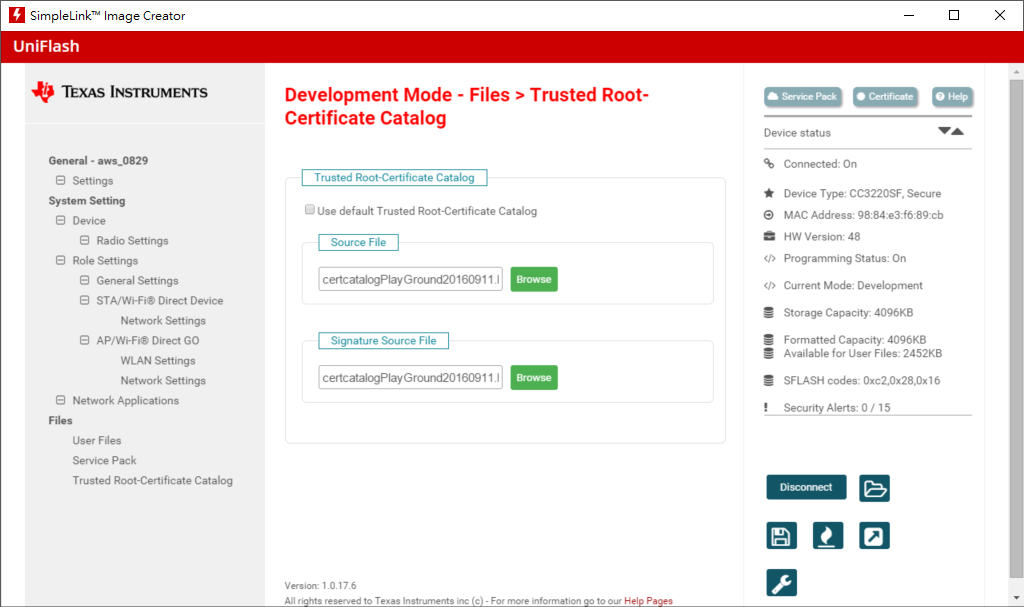
Step4. add Trusted Root-Certificate Catalog.
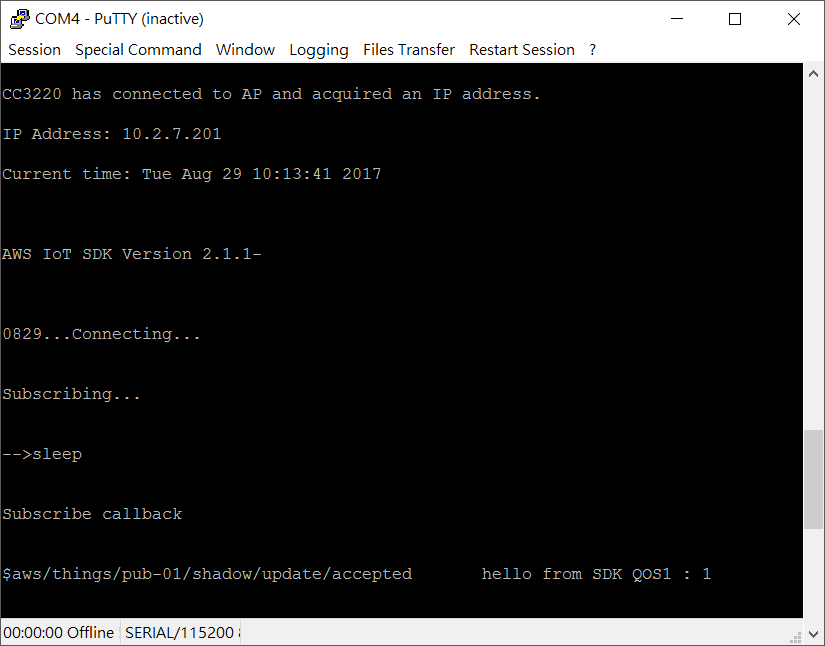
Step5. Successfully connect to AWS IoT
I am confused by some question below:
1. In step1, why did I need to select Private Key File Name:dummy-root-ca-cert-key and Certification File Name:dummy-root-ca-cert when I select MCU image (subscribe_publish_sample_CC3220SF_LAUNCHXL_tirtos_ccs.bin (mcuflashimg.bin)
2. In step2, the same Q1, I know that the root-ca.crt, xxx.certificate.pem.crt and xxx.private.pem.key are for SSL/TLS protocol, but why need to add dummy-root-ca-cert? What does that do?
3. In step4, Why need to add Trusted Root-Certificate Catalog. What does that do?
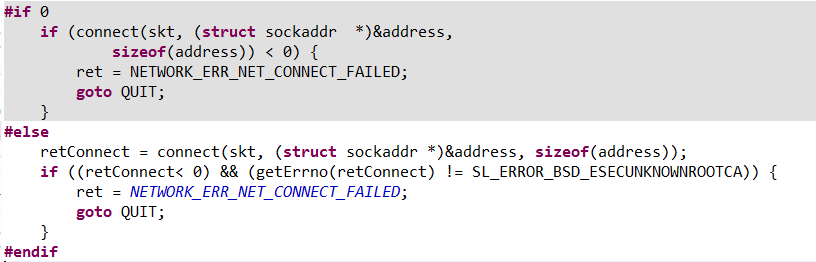
4. why need to change the code in network_sl.c
Thank you for being patient with me.