Hi,
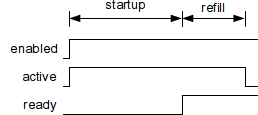
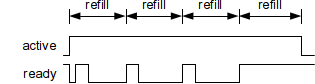
I tried to use Hardware RNG on my non-OS AM335x (non-OS programming reference: http://processors.wiki.ti.com/index.php/AM335X_StarterWare_Booting_And_Flashing)
I only found the setting about TRNG on AM335x with OS at http://processors.wiki.ti.com/index.php/Cryptography_Users_Guide
How can I set Hardware RNG in my C code? (toolchan:IAR)
Thanks!!