Hi Ti.
I'm using hex6x.exe from compiler 7.4.1(and the same result in compiler 7.4.8). After I processed the dsp0core3.out with it, I found that some data in the load get distorted with 2 bytes of 0 inserted. The way I call hex6x is :
hex6x -order L boot_script0.rmd dsp0core3.out
The rmd is as below:
-a
-boot
-e 0x10800000
-order L
ROMS
{
ROM1: org = 0x0000, length = 0x1000000, memwidth = 32, romwidth = 32
files = { boot_code0.btbl }
}
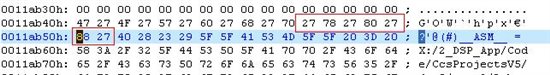
And the origin data in .out is as below figure:
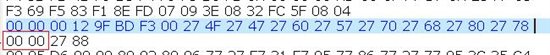
The data with 0 inserted is as below:
You can see 2 bytes of 0 in the middle.
All the files are included in the attachment so you guys may try it yourself. 4380.hex_err.rar