Other Parts Discussed in Thread: TMS320F280039C
Dear Experts,
I use the same setup condition to verify that the output of the network tool and MCU encryption is not the same.
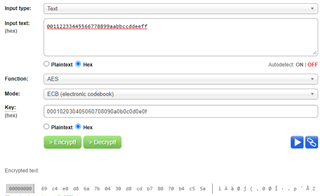
Mode setup: AES 128bit encrypt for ECB mode.
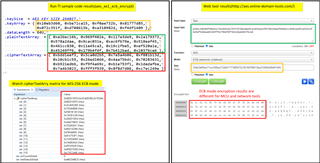
web tool url:aes.online-domain-tools.com/
MCU:TMS320F280039C and TI sample code(aes_ex1_ecb)
Why is the encryption of the AES module of the microcontroller different from the output of the online tool?
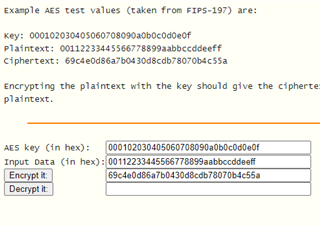
The encrypted output of the network encryption tool is as follows:
input data :{ 0x00112233, 0x44556677, 0x8899aabb, 0xccddeeff}
Key :{ 0x00010203, 0x04050607, 0x08090a0b, 0x0c0d0e0f}
Cypher:{ 0x69c4e0d8, 0x6a7b0430, 0xd8cdb780, 0x70b4c55a}
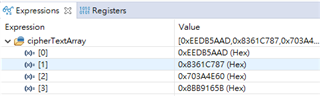
MCU TMS320F280039C output encryption results as follows:
input data :{ 0x00112233, 0x44556677, 0x8899aabb, 0xccddeeff}
Key :{ 0x00010203, 0x04050607, 0x08090a0b, 0x0c0d0e0f}
Cypher:{ 0xEEDB5AAD, 0x8361C787, 0x703A4E60, 0x8BB9165B}
Thanks for your help.