Part Number: TMS320F28027F
Other Parts Discussed in Thread: C2000WARE
Hi team,
Here're few questions from the customer may need your help:
1) Encryption generally succeeds when the TMS320f28027F is encrypted with the CCS11.2 version. However, the following reminder appears when decrypting, "Device unlocked. To clear the programd password, please erase sector A of Flash memory. " While Node A has chosen to erase, is it necessary to be under wait in bootload to unlock when decryption?
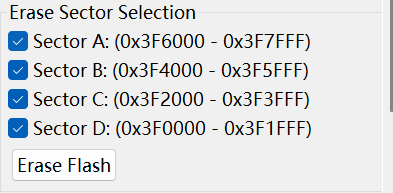
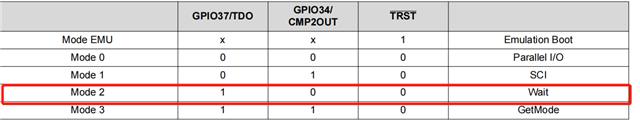
2) Why does some chips fail to work after encryption?
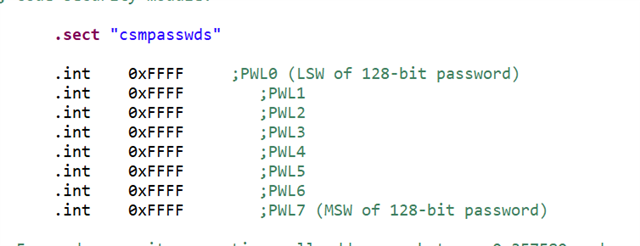
3) Adding the file _CSMpasswords.ASM, encrypting as a file, can the CCS on-chip flash password be emulated if the same password is used?
Could you help look into this case? Thanks.
Best Regards,
Cherry