Other Parts Discussed in Thread: C2000WARE, UNIFLASH, SYSCONFIG
Tool/software:
In our project, we have customer bootloader and application, now we want to use the API:CPU1BROM_calculateCMAC() in customer bootloader to verify the validity of application.
I have read the document <Application Report Secure BOOT on C2000 Device.pdf>.

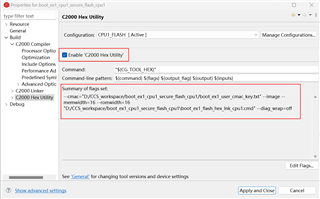
1、The first step is Generation of the authentication tag.
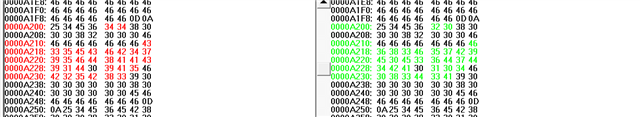
In my understand, the CMACKEY is inputed by "boot_ex1_user_cmac_key.txt",
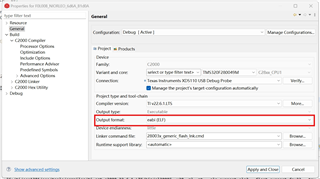
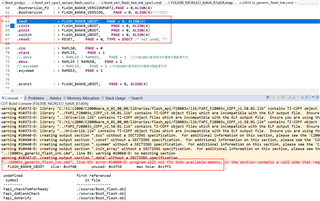
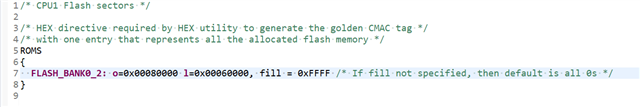
the length of application (such as: FLASH_BANK0_2: o=0x00084000 l=0x000B0000, fill = 0xFFFF) is inputed by "boot_ex1_flash_hex_lnk_cpu1.cmd".
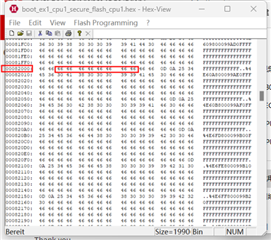
When we build application, the C2000 hex utility will run the CMAC algorithm and use the input message to generated Golden CMAC tag.
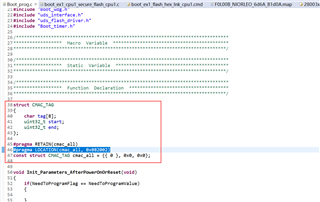
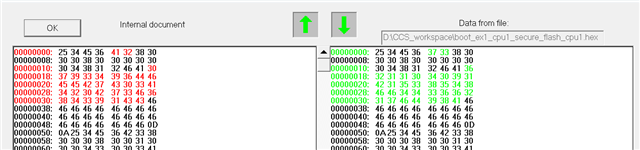
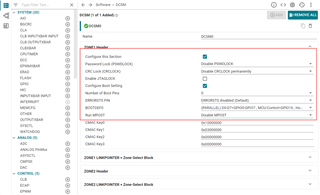
The the golden CMAC tag will be placed in "cmac_all" area? The "cmac_all" area is defined in customer bootloader or application?
2、The second step is Authentication of the application boot code in flash.
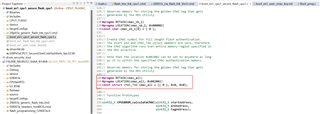
When run the customer bootloader, call the the API function:CPU1BROM_calculateCMAC() to compare tag generated by the CMAC algorithm and Golden CMAC tag.
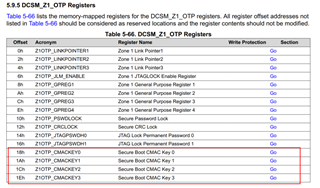
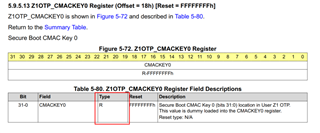
But where is the reference key defined?