Other Parts Discussed in Thread: C2000WARE, CONTROLSUITE
Tool/software: Code Composer Studio
Greetings,
I have been tasked with implementing the Code Security Module on our TMS320F28032 Chip. From reading about it I have a few questions in how I implement this. Here is what I think. I don't want to implement anything until I am certain this will not brick the chip up.
1. I have to go into the DSP2803x_SysCtrl.c and Change the CsmUnlock function to the password we want to use.
2. I have The code from the manuals
void dspUnsecure (void)
{
volatile int *CSM = (volatile int *)0x000AE0; //CSM register file
volatile int *PWL = (volatile int *)0x003F7FF8; //Password location
volatile int tmp;
int I;
// Read the 128-bits of the password locations (PWL)
// in flash at address 0x3F 7FF8 - 0x3F 7FFF
// If the device is secure, then the values read will
// not actually be loaded into the temp variable, so
// this is called a dummy read.
for (I=0; I<8; I++) tmp = *PWL++;
// If the password locations (PWL) are all = ones (0xFFFF),
// then the device will now be unsecure. If the password
// is not all ones (0xFFFF), then the code below is required
// to unsecure the CSM.
// Write the 128-bit password to the KEY registers
// If this password matches that stored in the
// PWL then the CSM will become unsecure. If it does not
// match, then the device will remain secure.
// An example password of:
// 0x11112222333344445555666677778888 is used.
EALLOW; // Key registers are EALLOW protected
*CSM++ = 0x1111; // Register KEY0 at 0xAE0
*CSM++ = 0x2222; // Register KEY1 at 0xAE1
*CSM++ = 0x3333; // Register KEY2 at 0xAE2
*CSM++ = 0x4444; // Register KEY3 at 0xAE3
*CSM++ = 0x5555; // Register KEY4 at 0xAE4
*CSM++ = 0x6666; // Register KEY5 at 0xAE5
*CSM++ = 0x7777; // Register KEY6 at 0xAE6
*CSM++ = 0x8888; // Register KEY7 at 0xAE7
EDIS;
}
void dspSecure (void)
{
volatile int *CSMSCR = 0x00AEF; //CSMSCR register
//Set FORCESEC bit
EALLOW; //CSMSCR register is EALLOW protected.
*CSMSCR = 0x8000;
EDIS;
}
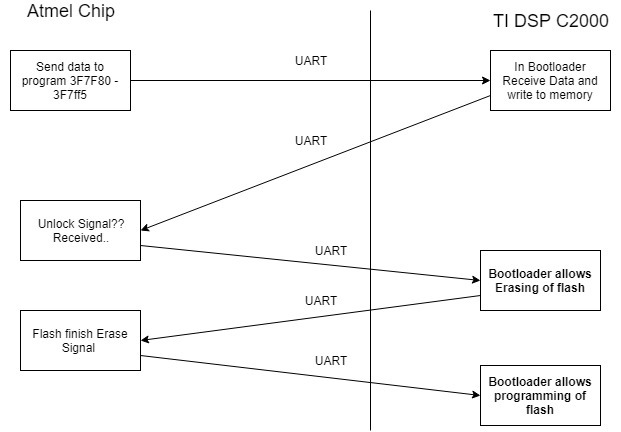
Once this implemented How do I go about unlocking and locking the chip. We are programming the device via UART from another chip which may throw an wrench into the system. Can someone explain to me the process of unlocking and locking the chip?
Thanks!