Hi,
I am almost in end stages of completing a bootloader for C2000 Cortex M3 core. I require some help with regards to an issue i am facing in making a jump to application section of flash from Bootloader.
What I have so far:
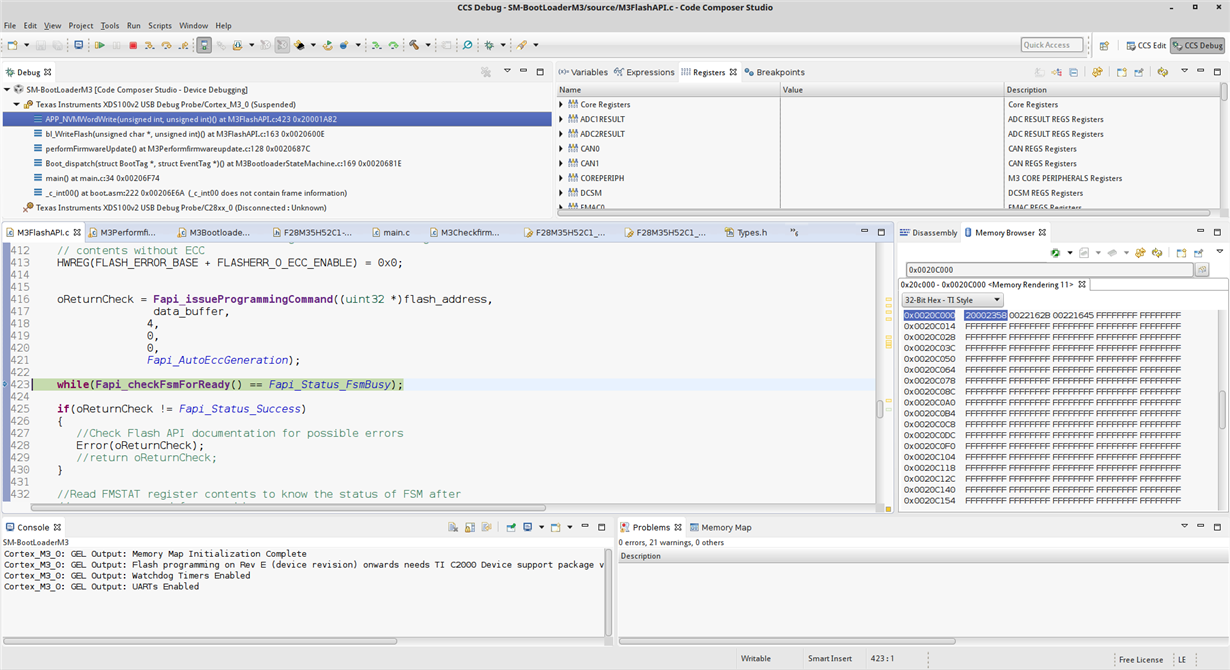
The bootloader has the ability now to read the data received through UART, parse the data and flash the data in to concerned address using TI Flash api library. For simplicity sake i have considered blinky m3 example to flash the from the Bootloader. I have selected intel HEX format with 32bit wide ROM and memory range. I am trying to send this generated HEX file using a python code from my host machine.
Flash Memory Sectors considered:
Bootoader -> Sector N, M and L
Application -> Sectors K to A.
Issue i am facing:
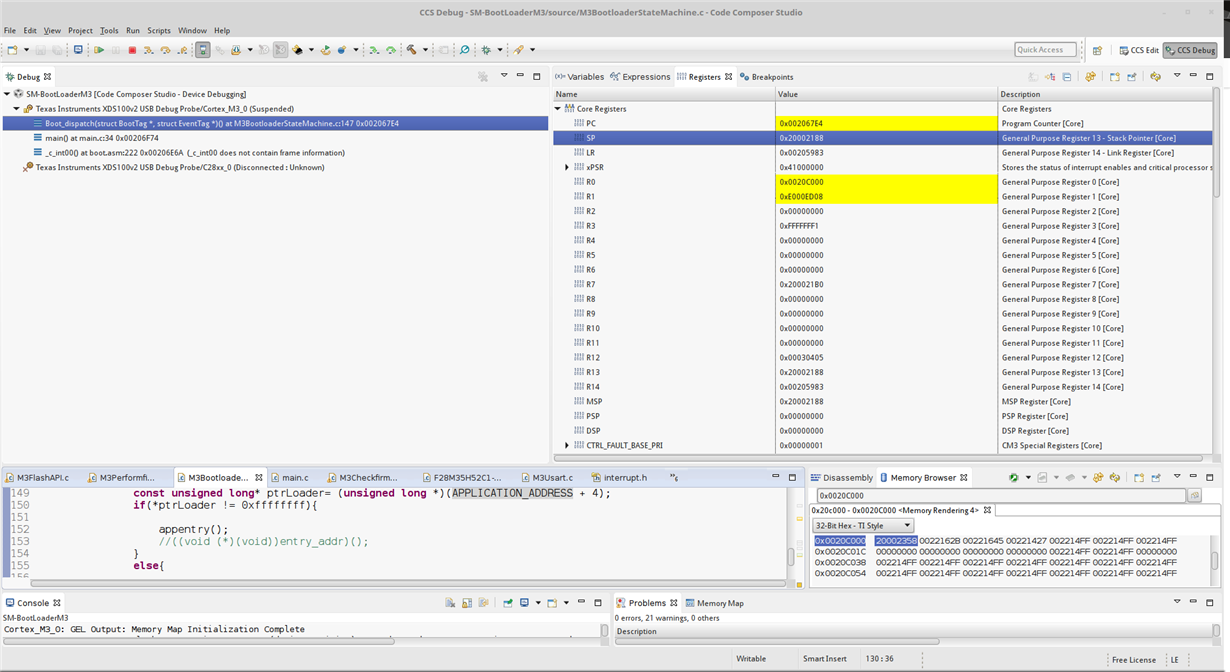
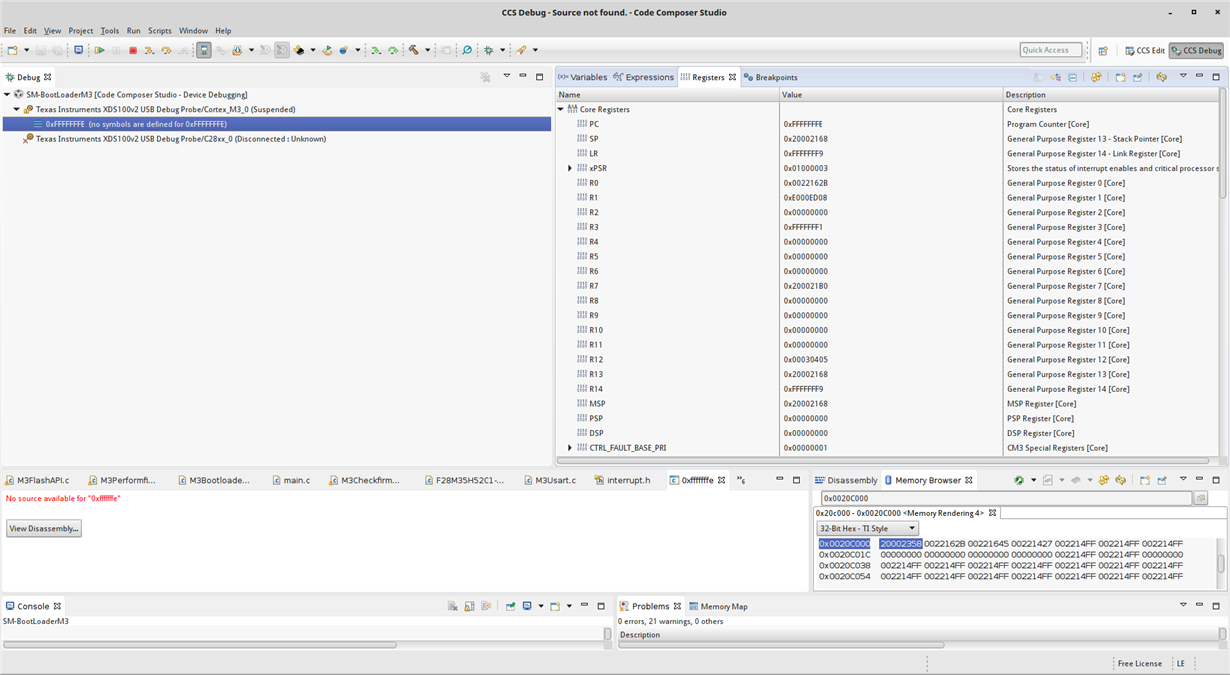
Once I write the respective parsed hex file in to the Flash memory and try to make a jump in to the blinky application the console throws a message saying "No content in location 0xfffffffe". But my reset vector for blinky application lies in location 0x0022162B and this is where i am trying to jump. I could see the contents in Disassembly window as well.
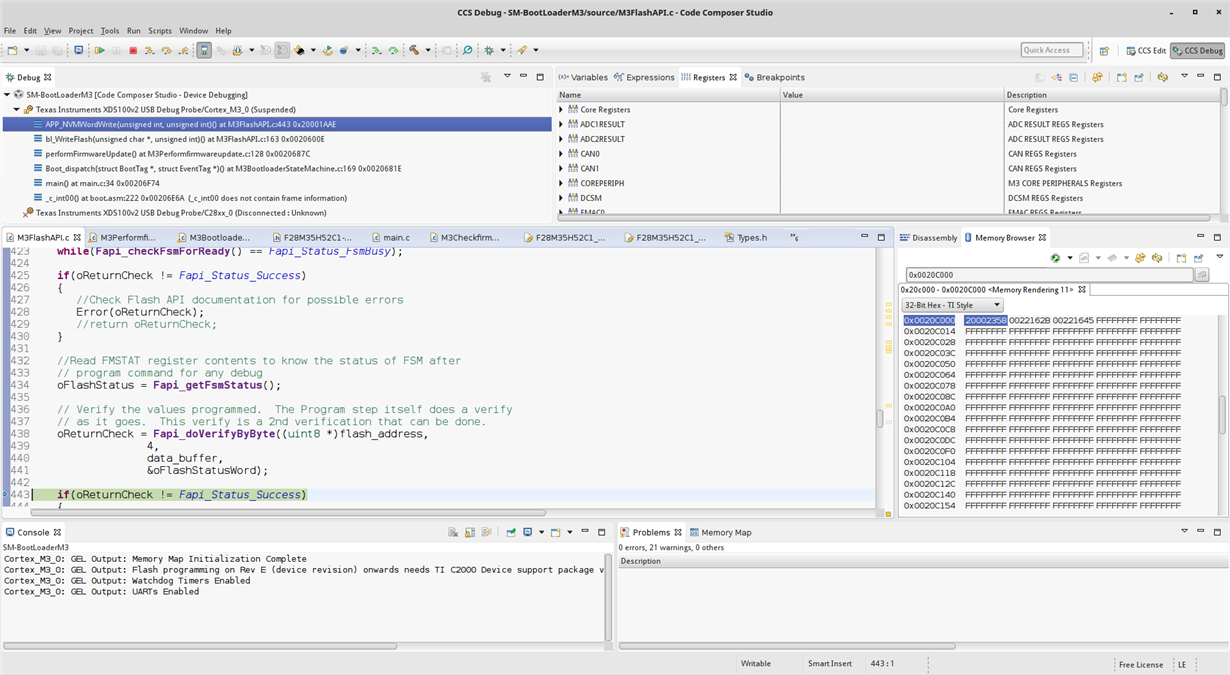
But what was not making sense was stack end address value of blinky application. This particular value when looked in vector table inside Memory region window after flashing is 0x20002358. But when i try to read the value from the Bootloader the value is 0x21002358 !! I can not understand whats going on here as i see the rite value in Flash Memory region but different value when i read it through software ??
Some Troubleshooting:
When i flash the blinky application program using TI flash utility by specifing sectors K to A and flashing Bottloader which is specifically for sectors N to L with out erasing blinky application, i could easily jump to blinky application with same reset vector address. But with out a problem in reading the stack end address which appears to be same as the one in Vector table.
But the problem seems to occur if i try to erase and write the flash contents through Bootloader and try to make a jump.
Below are some screenshots.
1. This is where i have captured appstack value. which shows a comparison btw what i read and whats in vector table address.
2. What i see when i make a jump from Bootloader
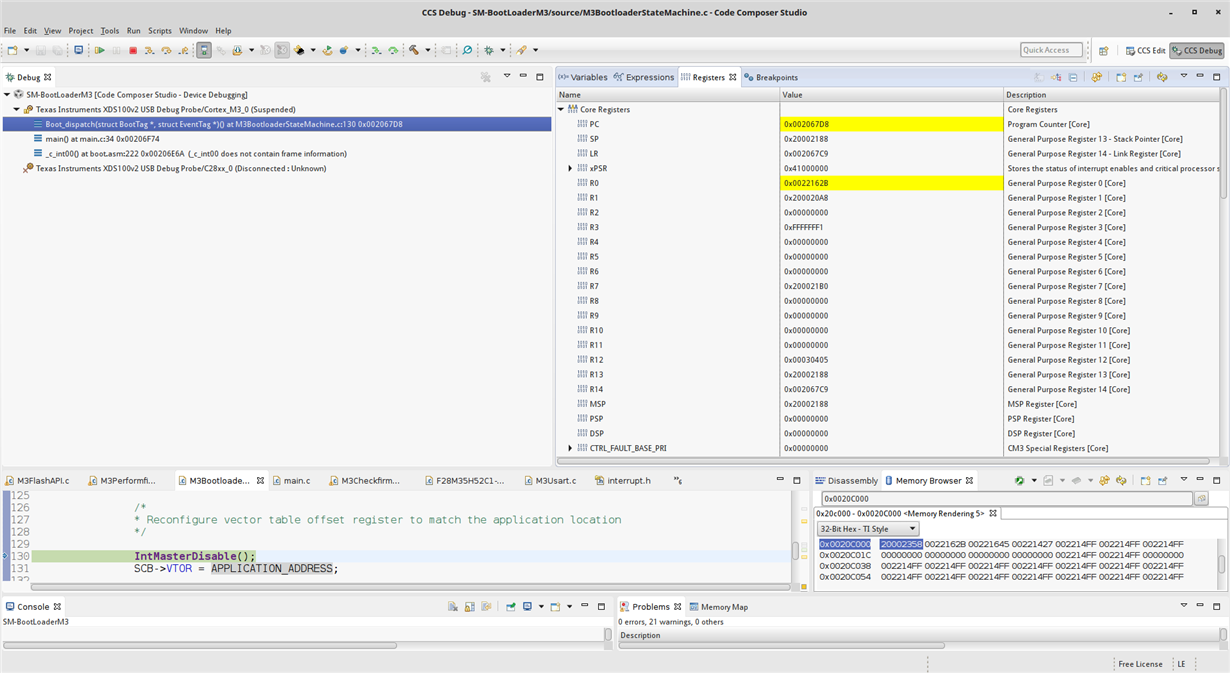
3. I tried to have a breakpoint on 0x0022162b to try step by step debugging in disassembly but this seem to not work for me either.
Thanks