Dear Sir:
I was hoping someone at TI can answer this question:
I own many MSP4305529 Launchpads. They all work fine in my CCS IDE, except for one.
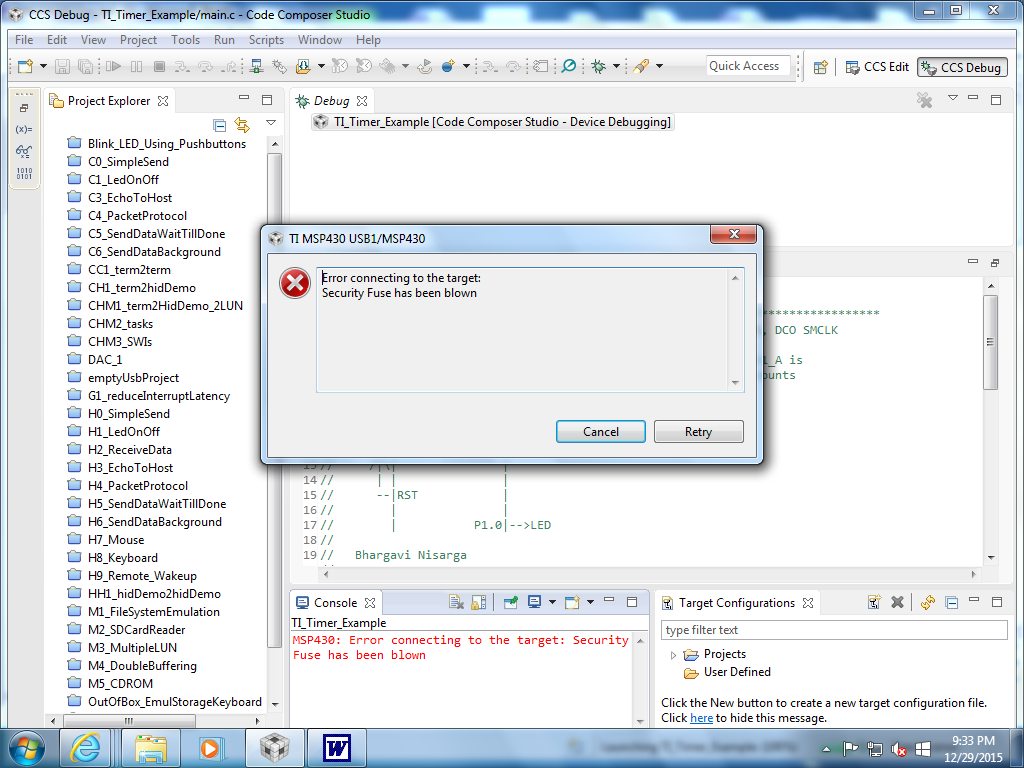
When I try to download a program onto the Launchpad I receive this message in CCS:
MSP430: Error connecting to the target: Unknown device
Recently, I used the TI Python Firmware Upgrader and tried the bootstrap loader option and the launchpad that was returning the error message now operates correctly according to the program that was downloaded. However, when I still attempt to use the program in the MSP430 CCS IDE, I still get the that same error message - " Error connecting to the target: Unknown device ".
I was hoping that someone at TI can recognize the source of the problem.
If there exists a maintenance software program in a format so that I can I use the TI Python Firmware Upgrader or other MSP430 flashing program, to reset the MSP430 (reset every memory location) can you please link me to the program?
Also, f there exists a maintenance software program such that the bootstrap loader can be utilized to check the hardware on the MSP430F5529 or the other IC's on the MSP430F5529 launchpad can you please link me to the program?