Hello,
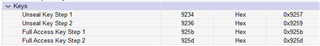
I am using a BQ7694201 device and need to select values to use for the security keys.
To transition between the security modes the keys must be written consecutively to the sub-command address (0x3E and 0x3F). The process to execute a sub-command requires writing the appropriate command value to the sub-command address so I was wondering if this places a restriction on the values that can be used for the Unseal and Full Access keys? Specifically, is it permitted to select a key value that has the same value as one of the commands that is listed in the 'Subcommands Table' of the device reference manual?
Thank you.
Steve