I'm trying to utilize the MPUs on the OMAP L138. I'm having trouble getting it to do anything.
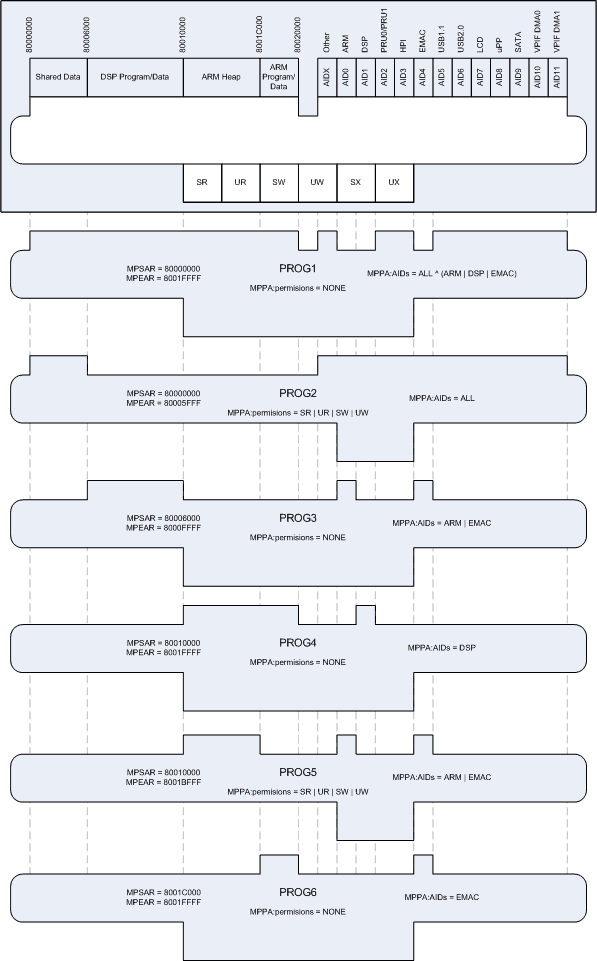
I'm trying to test MPU1 which serves the L3 shared RAM. MPU1 has 6 programmable ranges.
I'm running code on the ARM to configure and test MPU1. It's configuring 4 of the six ranges as follows:
| Range # | MPSAR (Start Address) | MPEAR (End Address) | MPPA | MPPA->AIDs | MPPA->Access Types |
| 0 | 0x80000000 | 0x80002FFF | 0x00000C36 | ARM, DSP | SR, SW, UR, UW |
| 1 | 0x80003000 | 0x80005FFF | 0x00000C36 | ARM, DSP | SR, SW, UR, UW |
| 2 | 0x80006000 | 0x8000FFFF | 0x0000083F | DSP | SR, SW, SX, UR, UW, UX |
| 3 | 0x80010000 | 0x8001FFFF | 0x0000043F | ARM | SR, SW, SX, UR, UW, UX |
I've tried both leaving the remaining two ranges at their defaults of:
| Range # | MPSAR (Start Address) | MPEAR (End Address) | MPPA | MPPA->AIDs | MPPA->Access Types |
| 4 | 0x80000000 | 0x8001FFFF | 0x03FFFEBF | All | All |
| 5 | 0x80000000 | 0x8001FFFF | 0x03FFFEBF | All | All |
And I've tried configuring the remaining two ranges as follows:
| Range # | MPSAR (Start Address) | MPEAR (End Address) | MPPA | MPPA->AIDs | MPPA->Access Types |
| 4 | 0x80000000 | 0x8001FFFF | 0x00000000 | None | None |
| 5 | 0x80000000 | 0x8001FFFF | 0x00000000 | None | None |
After configuring the ranges in MPU1, the code then enables interrupts by setting the PROTERR_EN bit (bit 0) in IENSET of MPU1 and setting the PROTERR_EN bit (bit 0) in IENSET of SYSCFG0.
Then to test the protection, my code (running on the ARM) tries to write to 0x80006000, which I would expect the MPU to prevent. But, the MPU doesn't prevent the write, and it doesn't signal an interrupt and there is nothing in it's FLTSTAT and FLTADDR registers after this. It's as if the MPU isn't doing anything.
Is there some step I'm missing to enable the MPU?
I thought maybe running this test code with the debugger / emulator might be an issue, so I've tried running it booted from SPI FLASH, but the MPU still doesn't prevent the ARM from writing to that address.
Anyone have any insight?
Thanks,
Arthur