Other Parts Discussed in Thread: SYSBIOS
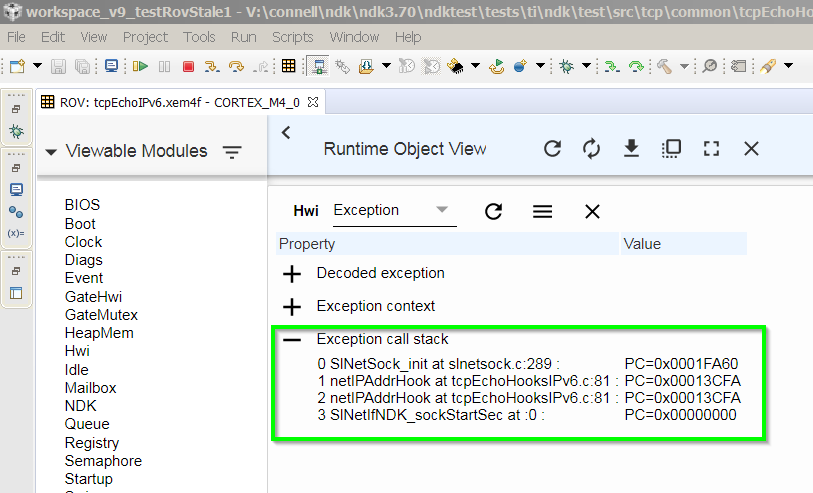
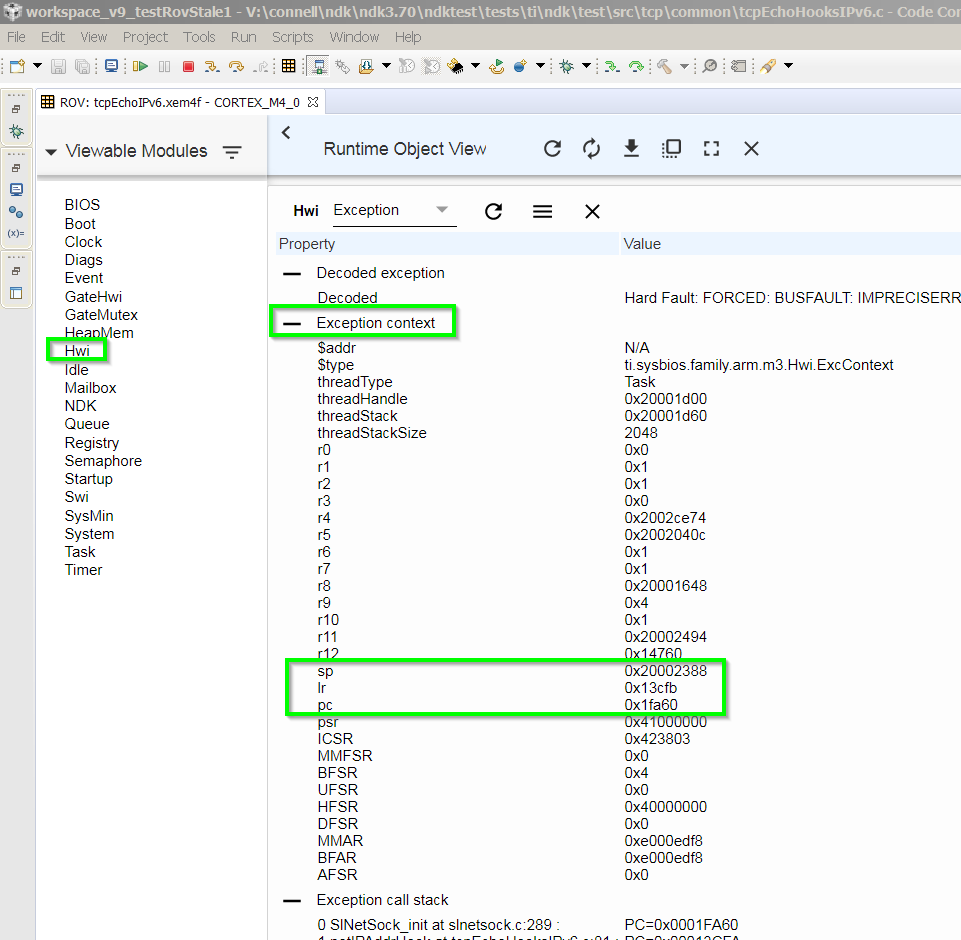
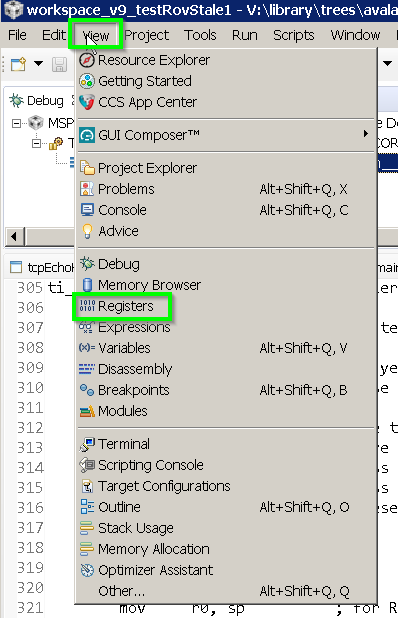
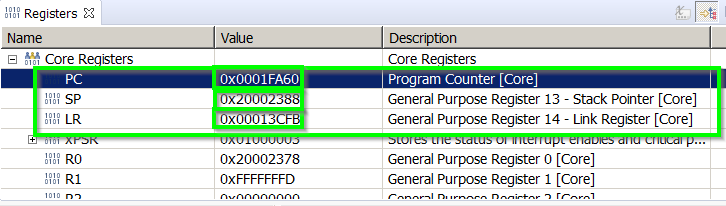
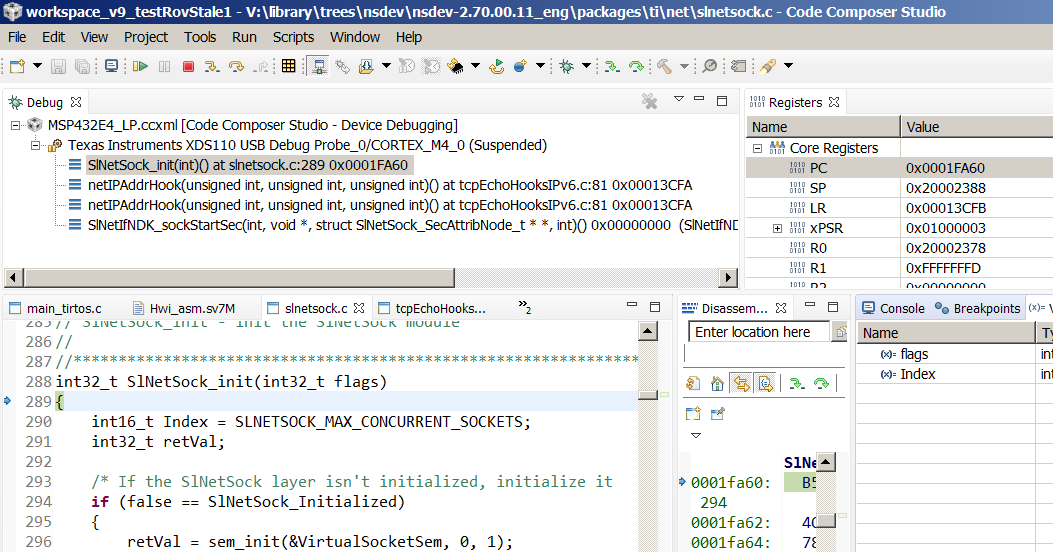
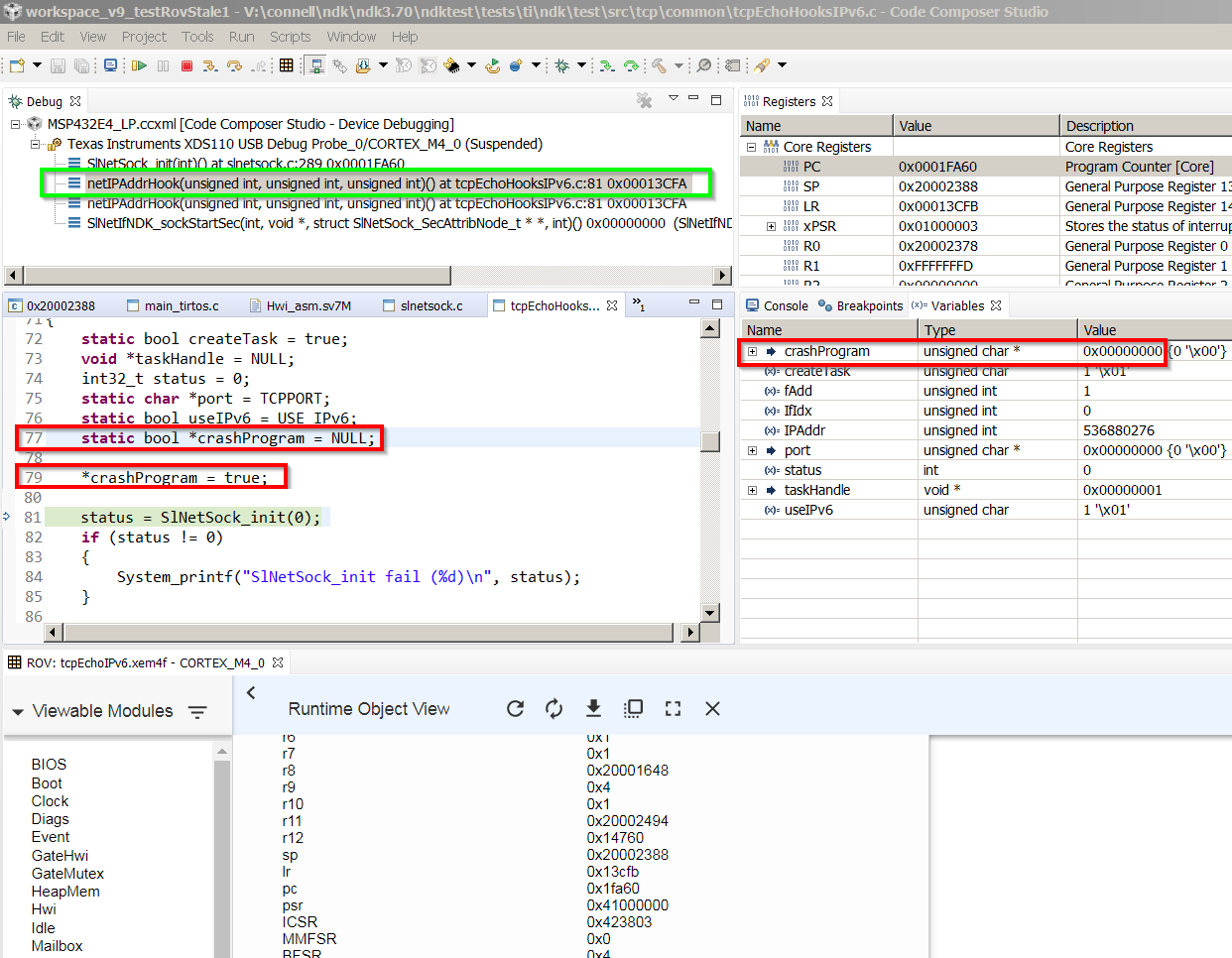
I ran my program and it seemed to "hang". When I halted it in CCS, I saw that the program was stuck spinning in an infinite loop within the following function:
ti_sysbios_family_arm_m3_Hwi_excHandlerAsm__I()
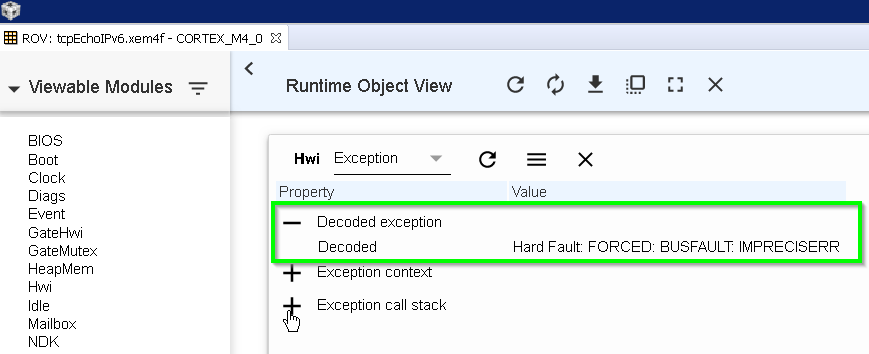
How can I find the cause of this?