Other Parts Discussed in Thread: BLE-STACK
Hi.
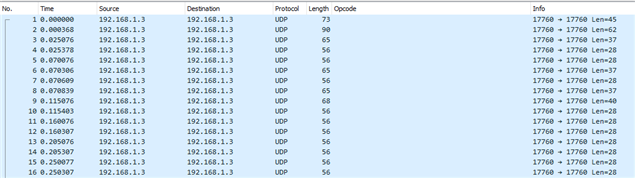
We are having some problems holding longer connections to some Android devices. The connection abruptly ends after about 900 connection events (about 40s with default Android 45ms interval and 20min with our preferred 145ms interval and latency of 10). The disconnect reason given by the TI Stack is LL_STATUS_ERROR_LL_TIMEOUT (0x22). After searching through the forums I tried disabling Data Length Extension in the local feature set after which the connections seems to hold. I've attached sniffer traces for both cases, where the peripheral is running SimplePeripheral from SDK 6.20.00.29 (with slight modification to disable DLE, use public addresses and disable the connection parameter request).
I'm looking for answers to the following questions:
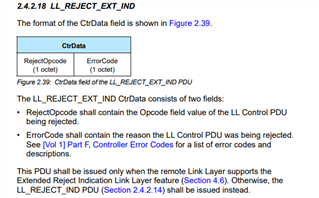
1. Based on the results of the forum search, the current assumption is that the BLE-Stack of the Android devices is faulty. Since disabling DLE in the local feature set seems to make it work, the problem seems to be connected to the LL_LENGTH_REQ send by the peripheral which is responded with an LL_REJECT_EXT_IND by the Android device. Can you point out the error here? Is LL_REJECT_EXT_IND not a valid response to a LL_LENGTH_REQ? I've tried looking through the BLE Specification, but was unable to determine a definite answer which responses are valid here. This would help in communcation with the supplier of the Android devices.
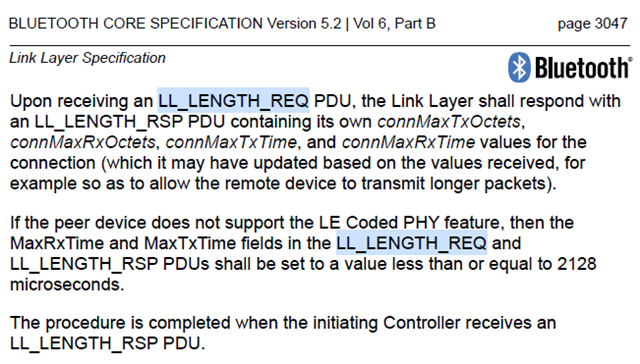
2. In the working trace the central still sends a LL_LENGTH_REQ which is answered with 251/2120ms bounds by the peripheral. Does this mean that the connection can still profit from larger payloads although the DLE bit in the local feature set is cleared? If yes this would make this approach a valid workaround.
3. In the BLE Specification the LL response timeout is given as 40s (Vol 6, Part B, Section 5.2). Why does the timeout change with the connection parameters in our case?
Sincerely,
Alexander Wenner