Other Parts Discussed in Thread: SYSCONFIG, AES-128
Tool/software:
When I try to perform cryptographic operations with the following source code, the return value of psa_crypto_init() is -147 (PSA_ERROR_HARDWARE_FAILURE).
After that, the return value of psa_import_key() becomes -141 (PSA_ERROR_INSUFFICIENT_MEMORY) and cannot import. What is the cause and how can I fix it?
This code is a rewrite of the sample code empty.c.
The environment used is as follows:
・Bord : CC2745R10-Q1
・Debugger : XDS110 SDK : SimpleLink Lowpower f3 ver.8.40.2
・IDE : Code Composer Studio ver.12.8.1
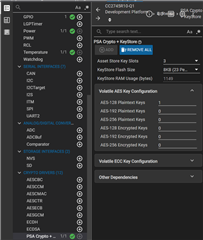
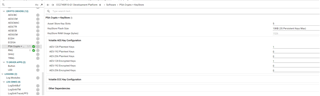
・syscongig : see bellow
#include <ti/drivers/cryptoutils/cryptokey/CryptoKeyKeyStore_PSA.h>
#include <ti/drivers/cryptoutils/cryptokey/CryptoKeyKeyStore_PSA_init.h>
#include <ti/drivers/cryptoutils/cryptokey/CryptoKeyKeyStore_PSA_helpers.h>
#include <ti/drivers/AESCBC.h>
void *mainThread(void *arg0)
{
uint8_t keyingMaterial[16] = {0x1f, 0x8e, 0x49, 0x73, 0x95, 0x3f, 0x3f, 0xb0,
0xbd, 0x6b, 0x16, 0x66, 0x2e, 0x9a, 0x3c, 0x17};
uint8_t KeyExportData[16] = {0};
size_t ExportDataLength;
CryptoKey cryptoKey;
mbedtls_svc_key_id_t keyID;
int_fast16_t status;
psa_key_attributes_t attributes = PSA_KEY_ATTRIBUTES_INIT;
AESCBC_Handle handle;
AESCBC_OneStepOperation operation;
int_fast16_t encryptionResult;
uint8_t iv[16] = {0x2f, 0xe2, 0xb3, 0x33, 0xce, 0xda, 0x8f, 0x98,
0xf4, 0xa9, 0x9b, 0x40, 0xd2, 0xcd, 0x34, 0xa8};
uint8_t plaintext[16] = {0x45, 0xcf, 0x12, 0x96, 0x4f, 0xc8, 0x24, 0xab,
0x76, 0x61, 0x6a, 0xe2, 0xf4, 0xbf, 0x08, 0x22};
uint8_t ciphertext[sizeof(plaintext)];
uint8_t errFlg = 0;
status = psa_crypto_init();
// Assign key attributes
psa_set_key_usage_flags(&attributes, PSA_KEY_USAGE_ENCRYPT);
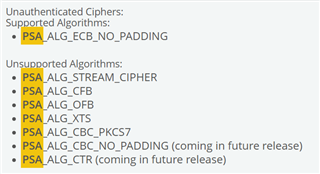
psa_set_key_algorithm(&attributes, PSA_ALG_CBC_NO_PADDING);
psa_set_key_type(&attributes, PSA_KEY_TYPE_AES);
psa_set_key_lifetime(&attributes, PSA_KEY_LIFETIME_PERSISTENT);
psa_set_key_bits(&attributes, 128);
// Set key ID
GET_KEY_ID(keyID, PSA_KEY_ID_USER_MIN);
psa_set_key_id(&attributes, keyID);
// Import the keyingMaterial
status = psa_import_key(&attributes, keyingMaterial, sizeof(keyingMaterial), &keyID);
if (status != PSA_SUCCESS)
{
errFlg = 1;
}
// Initialize cryptoKey for crypto operations
KeyStore_PSA_initKeyHSM(&cryptoKey, keyID, sizeof(keyingMaterial), NULL);
// Use the cryptoKey for AESCCM operations
handle = AESCBC_open(0, NULL);
AESCBC_OneStepOperation_init(&operation);
operation.key = &cryptoKey;
operation.input = plaintext;
operation.output = ciphertext;
operation.inputLength = sizeof(plaintext);
operation.iv = iv;
encryptionResult = AESCBC_oneStepEncrypt(handle, &operation);
AESCBC_close(handle);
status = psa_export_key(keyID, KeyExportData, 16, &ExportDataLength);
status = psa_import_key(&attributes, KeyExportData, sizeof(keyingMaterial), &keyID);
handle = AESCBC_open(0, NULL);
AESCBC_OneStepOperation_init(&operation);
operation.key = &cryptoKey;
operation.input = plaintext;
operation.output = ciphertext;
operation.inputLength = sizeof(plaintext);
operation.iv = iv;
encryptionResult = AESCBC_oneStepEncrypt(handle, &operation);
AESCBC_close(handle);
}