Tool/software:
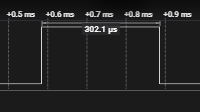
The SHA256 calculation time previously measured with SDK8.30 was about 0.2 ms, but when measured with SDK9.10, it took about 7 ms.
We also confirmed that other operations such as AES took about 7ms as well.
Is this a defensive measure to prevent identification of which operation is being performed by the operation time in anticipation of a side-channel attack?
Would it be possible to perform operations at the original speed by changing some settings?