Tool/software:
My environment is as follows:
Board: CC2745R10-Q1
Debugger: XDS110
SDK: SimpleLink Lowpower f3 ver.9.10.00.83
IDE: IAR Embedded Workbench for ARM 9.60.3.7274
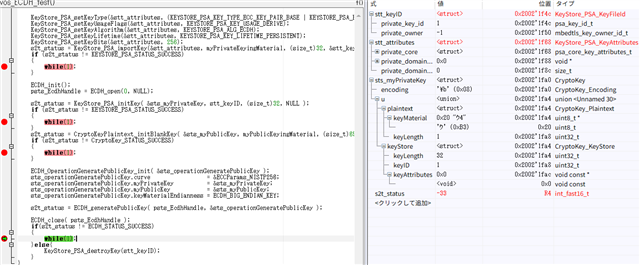
I'm trying to generate a public key from a private key stored in PSA storage,
but the value of s2t_status upon completion of ECDH_generatePublicKey() is -33.
How can I resolve this?
static uint8_t myPrivateKeyingMaterial[32] = {0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, \
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, \
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, \
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01 };
static uint8_t myPublicKeyingMaterial[65] = { 0 };
static void vos_ECDH_test()
{
KeyStore_PSA_KeyFileId stt_keyID;
KeyStore_PSA_KeyAttributes stt_attributes = KEYSTORE_PSA_KEY_ATTRIBUTES_INIT;
ECDH_OperationGeneratePublicKey sts_operationGeneratePublicKey;
CryptoKey sts_myPrivateKey;
CryptoKey sts_myPublicKey;
ECDH_Handle psts_EcdhHandle;
int_fast16_t s2t_status;
s2t_status = psa_crypto_init();
if (s2t_status != PSA_SUCCESS)
{
while(1);
}
s2t_status = HSMLPF3_provisionHUK();
if (s2t_status != HSMLPF3_STATUS_SUCCESS)
{
while(1);
}
GET_KEY_ID(stt_keyID, KEYSTORE_PSA_KEY_ID_USER_MIN);
KeyStore_PSA_setKeyId(&stt_attributes, stt_keyID);
KeyStore_PSA_setKeyType(&stt_attributes, (KEYSTORE_PSA_KEY_TYPE_ECC_KEY_PAIR_BASE | KEYSTORE_PSA_ECC_CURVE_SECP256R1) );
KeyStore_PSA_setKeyUsageFlags(&stt_attributes, KEYSTORE_PSA_KEY_USAGE_DERIVE);
KeyStore_PSA_setKeyAlgorithm(&stt_attributes, KEYSTORE_PSA_ALG_ECDH);
KeyStore_PSA_setKeyLifetime(&stt_attributes, KEYSTORE_PSA_KEY_LIFETIME_PERSISTENT);
KeyStore_PSA_setKeyBits(&stt_attributes, 256);
s2t_status = KeyStore_PSA_importKey(&stt_attributes, myPrivateKeyingMaterial, (size_t)32, &stt_keyID);
if (s2t_status != KEYSTORE_PSA_STATUS_SUCCESS)
{
while(1);
}
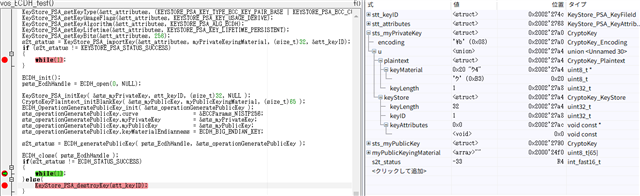
ECDH_init();
psts_EcdhHandle = ECDH_open(0, NULL);
KeyStore_PSA_initKey( &sts_myPrivateKey, stt_keyID, (size_t)32, NULL );
CryptoKeyPlaintext_initBlankKey( &sts_myPublicKey, myPublicKeyingMaterial, (size_t)65 );
ECDH_OperationGeneratePublicKey_init( &sts_operationGeneratePublicKey );
sts_operationGeneratePublicKey.curve = &ECCParams_NISTP256;
sts_operationGeneratePublicKey.myPrivateKey = &sts_myPrivateKey;
sts_operationGeneratePublicKey.myPublicKey = &sts_myPublicKey;
sts_operationGeneratePublicKey.keyMaterialEndianness = ECDH_BIG_ENDIAN_KEY;
s2t_status = ECDH_generatePublicKey( psts_EcdhHandle, &sts_operationGeneratePublicKey );
ECDH_close( psts_EcdhHandle );
if(s2t_status != ECDH_STATUS_SUCCESS)
{
while(1);
}else{
KeyStore_PSA_destroyKey(stt_keyID);
}
}