Other Parts Discussed in Thread: SYSCONFIG
Tool/software:
Hello,
My environment is as follows:
Board: CC2745R10-Q1
Debugger: XDS110
SDK: SimpleLink Lowpower f3 ver.9.10.00.83
IDE: IAR Embedded Workbench for ARM 9.60.3.7274
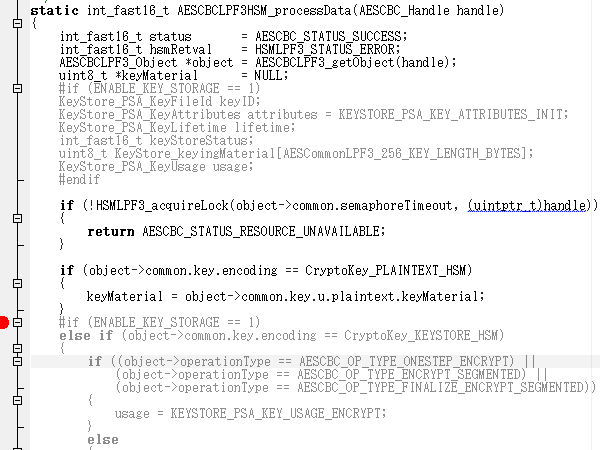
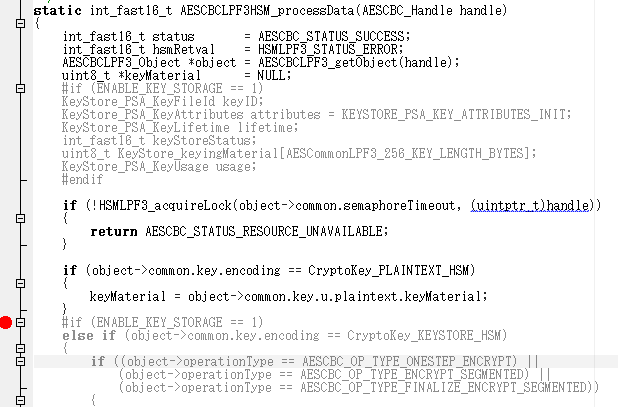
Looking at the SDK source, it only processes key encodings CryptoKey_PLAINTEXT_HSM or CryptoKey_KEYSTORE_HSM.
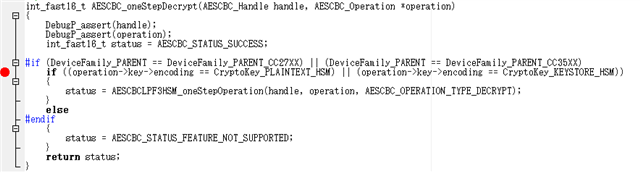
Does this mean that CBC decryption is not possible unless the key is stored on an HSM?
Is it possible to perform CBC decryption using a key stored in PSA storage (with a lifetime of KEYSTORE_PSA_KEY_LIFETIME_PERSISTENT)?
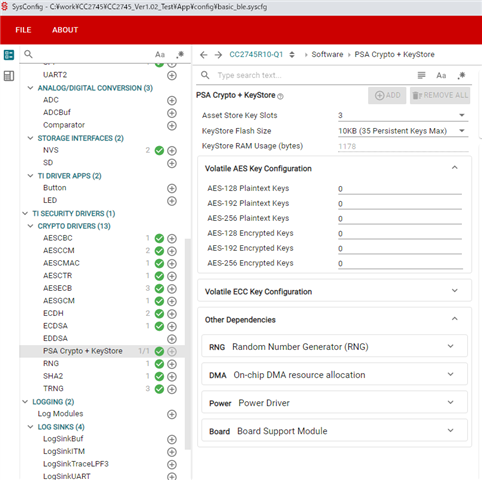
Also, could you tell me how to enable ENABLE_KEY_STORAGE (a SysConfig setting?)?
※If the key encoding is CryptoKey_KEYSTORE_HSM, ENABLE_KEY_STORAGE must be enabled in the compilation software.
Best,