Hello,
We are testing the LE Secure Connections Just Works pairing. We have our BLE device CC2640 configured in peripheral role and connecting with a Pixel Smartphone running Android 9.0 and nRF Connect app.
Our configuration is as follows:
- CCS 7.4.0
- BLE Stack ble_sdk_2_02_02_25 (Version 2.2.2)
- Compiler TI ARM Compiler v16.9.4 LTS
- LE SC set to GAPBOND_SECURE_CONNECTION_ONLY
- MITM set to false
- IO Capabilities set to No Display No Keyboard
We have all our characteristics set with read and write authentication required setting, this means the moment we attempt a read using nRF Connect using the Smartphone, the pairing process begins. It seems the pairing process is successful and we even receive the corresponding callback from gapbondmgr passing a pairing success code for a pairing complete event. 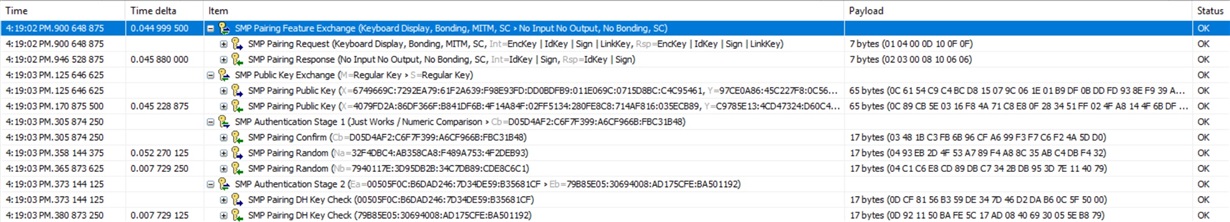
However, the issue we are observing is that we cannot get any data at all from any characteristic after the pairing process is completed and the link encryption is started. We observe our peripheral device is sending a "Start Encryption Request" every time as a result for a reading request coming from the master.
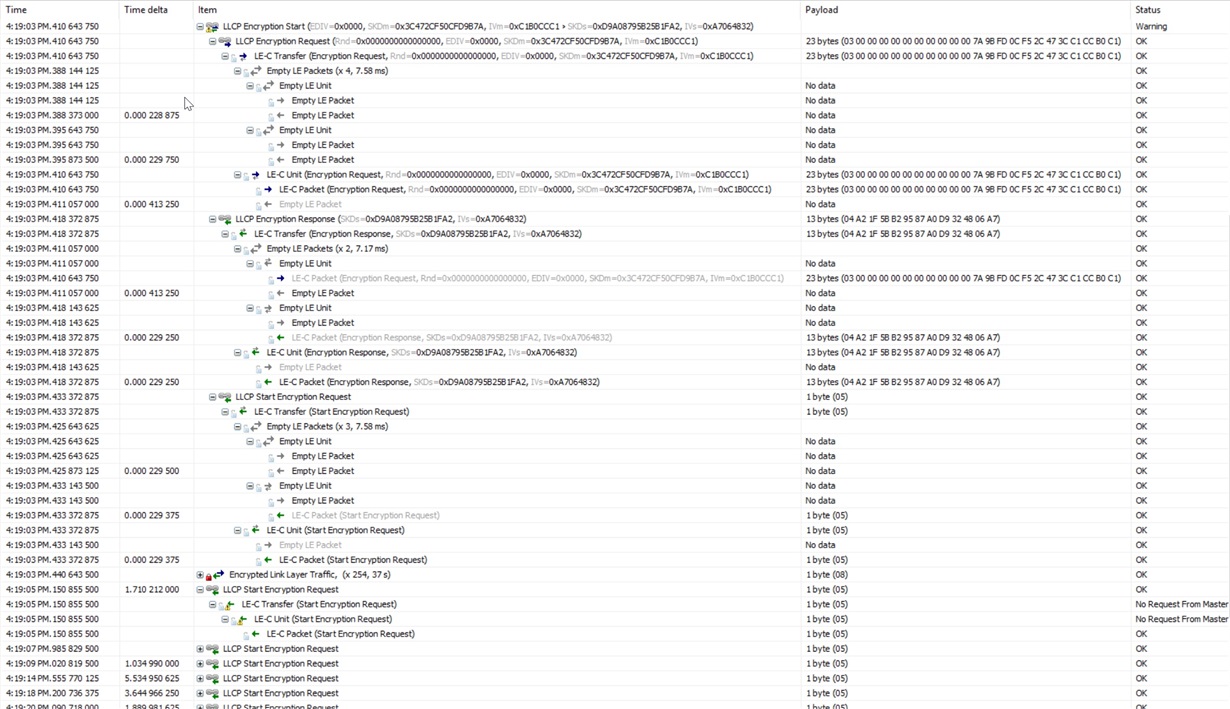
In the following trace, the Bluetooth sniffer shows that the initial encryption process sequence is apparently incomplete. However, we know that this part of the pairing is handled entirely by the stack.We have also verified there are no heap memory allocation issues when this happens. Here is a screenshot of the trace right after the one shown above after sharing the keys and the checks were successful:
The warning sign for the "LLCP Encryption Start" row says "Incomplete Sequence". After the pairing process is over, we can see the "Encrypted Link Layer Traffic" packets. Then, every time a read attempt is executed using the nRF Connect app on the Smartphone, we observe the event shown in this picture at the bottom "LLCP Start Encryption Request". One per reading attempt. The Bluetooth sniffer shows a "No Request From Master" warning when this happens.
Is it possible that the stack actually missed something during the initial encryption start process and that's why the Bluetooth sniffer is giving an "Incomplete Sequence" warning and hence we cannot read any characteristics data at all?
Ricardo Bello