Other Parts Discussed in Thread: LAUNCHXL-CC26X2R1
Tool/software: TI-RTOS
Hello,
I'v having trouble debugging my application. First a few specifics:
My application is expanded upon the Project_zero Bluetooth 5 project using the CC2642R1F Rev C. chip on a LAUNCHXL-CC26X2R1 Dev kit. (Rev B.) on the 2.30 SDK.
As a note i do have access to the Rev E. CC2642R1F chip and the latest SDK (3.10)
I am using CCS 9.0.1 on Windows 10.
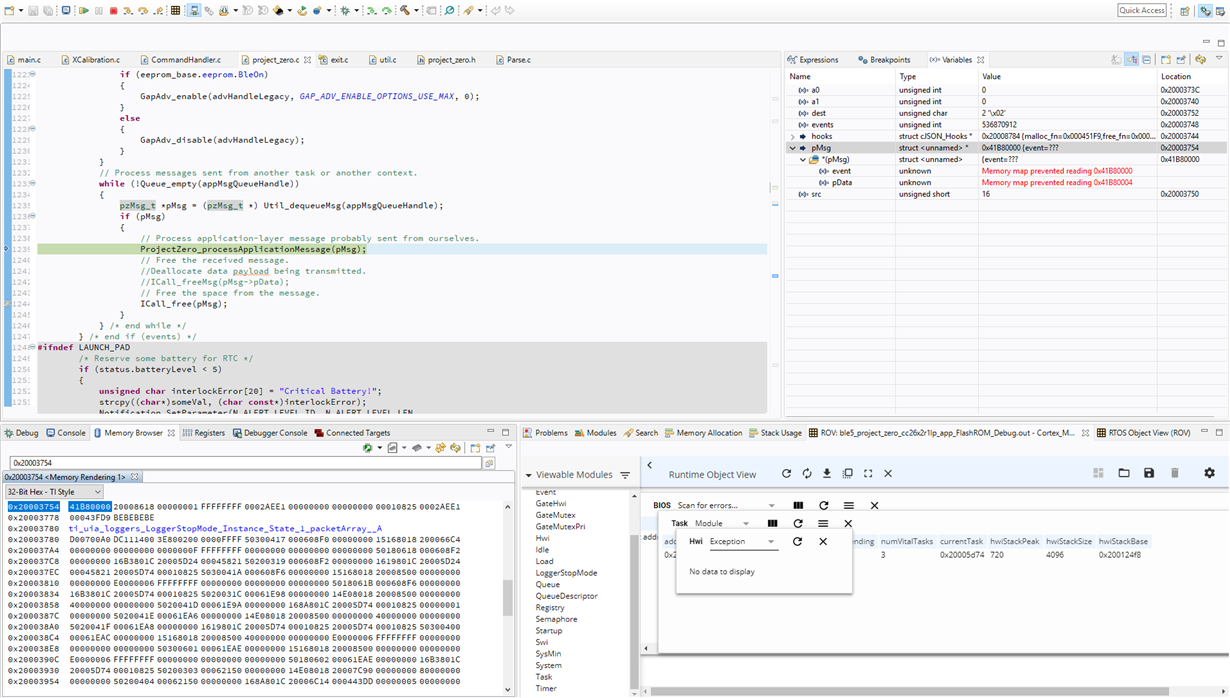
The specific issues is that my App Msg queue in the Project_Zero Task appears to be corrupted after a long running computation. In detail, it appears that a message (of type pzMsg_t) had been de-allocated and is now pointing to memory outside of the memory map declarations.
Here is watch in the debugger:
Whats more interesting is that if i remove this for loop from the execution loop, my AppMsg queue is not corrupted:
void ToWavenumberCubic(uint16_t* pixelData, bool isCalibration, float* extended)
{
for (int i = 0; i < 1024; i++)
{
extended[i] = pixelData[i];
}
}
//Additional Code removed for brevity
Before this function there is much more computation, but this section seems to trigger the error. (If i remove the earlier computations and still run the above code, there is no error). I don't believe the above function uses any additional stack or heap. Casting may be an issue.
I have tried wrapping the long running code in an ICall_enterCriticalSection, so that HWI/SWI interrupts are not sent to the AppMsg Queue. I also turn off Clock interrupts.
Additional Thoughts:
I do not believe this is a Heap issue as i am watching the heapmgr expressions and do not see a failed allocation.
It appears the pMsg is allocated early on in the stack before the long-running code, as it appears early on in the stack.
Should i be using a different semaphore or perhaps a new task for computationally expensive code?
Perhaps either clear the msg queue or wait for it to be cleared before running computationally expensive code.
I'm just not sure how to debug from here, however i will continue to investigate stack or dealloc issues on that Msg.
Full project attached, please PM for password. The Calibrate_handler is the function where this behavior is seen (CommandHandler.c)
I greatly appreciate your time and expertise!
Thank you,
Brett