Hi Team, seeking some assistance for one of my customer.
I am not able to reproduce the screenshot of the Wireshark of Ti support in the link below:
The given screenshot by ti support in that thread is:
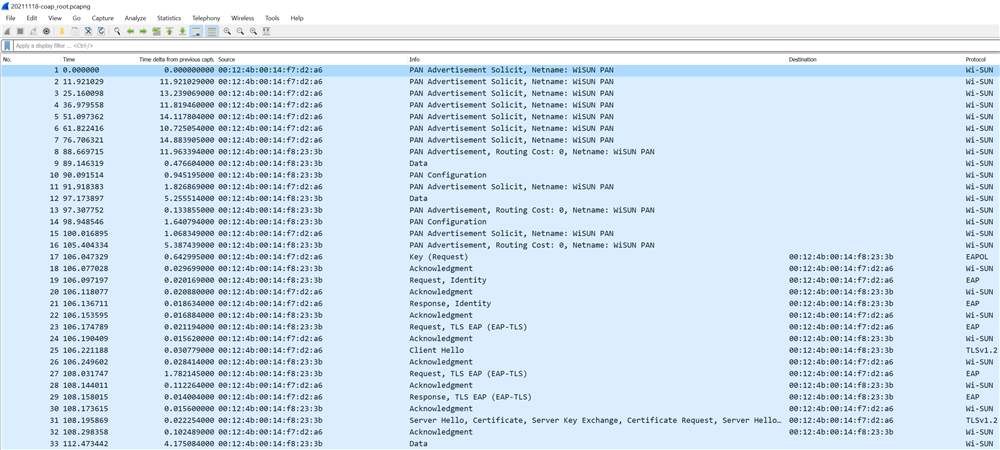
Indeed, when I totally followed the TI WISUN track debug information regarding launching the Sniffer2 tool and Wireshark:
my Wireshark looks like this:
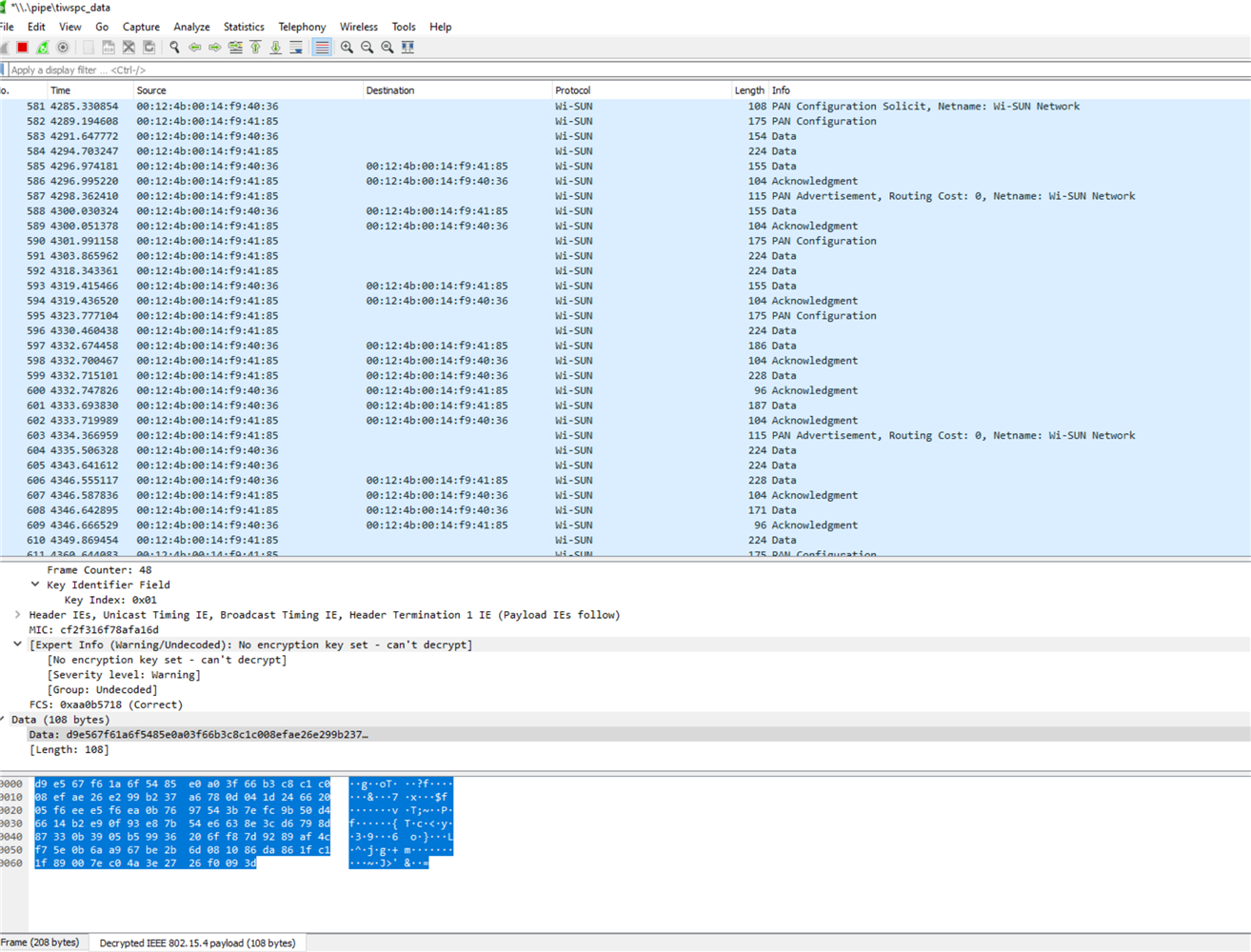
I must mention that I already compiled the ns_br and ns_node sources with "FIXED_GTK_KEYS" defined.
Very important note: I see some people have problem that Wireshark reports "Bad FCS" for every Wisun packet with the latest Sniffer and "Ti radio packet info" pipe. The problem is the "FCS Format in IEEE 802.15.4 settings in the Wireshark. This setting must be set to ITU-T-CRC-32 option. But please not that this is not resolving the problem I have with not showing EAPOL, requests, and responses of EAP / 4W and 2W security handshakes
I am using Ti CC13XX SDK 5.40 which is the latest version.
Thank you.