Other Parts Discussed in Thread: SYSCONFIG, CC1310
Hi,
I upgrade my system to TIRTOS7.
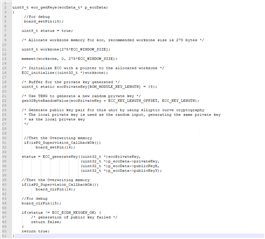
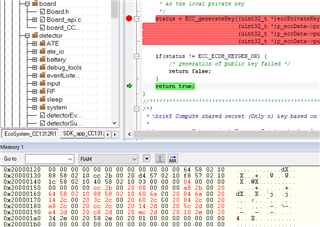
When I call to ECC_generateKey() i see overwriting memory on ram memory :
Addresses 0x2000014B- 0x200001b0
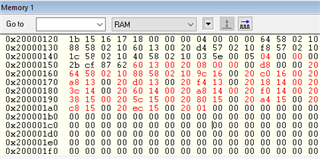
In map file you can see that this memory allocated to other parameters :
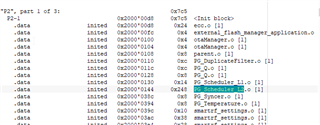
This problem not happened when I used with TIRTOS old version
Ho I can fixe it ?
Thank
Yaki
The running code :