Tool/software: Code Composer Studio
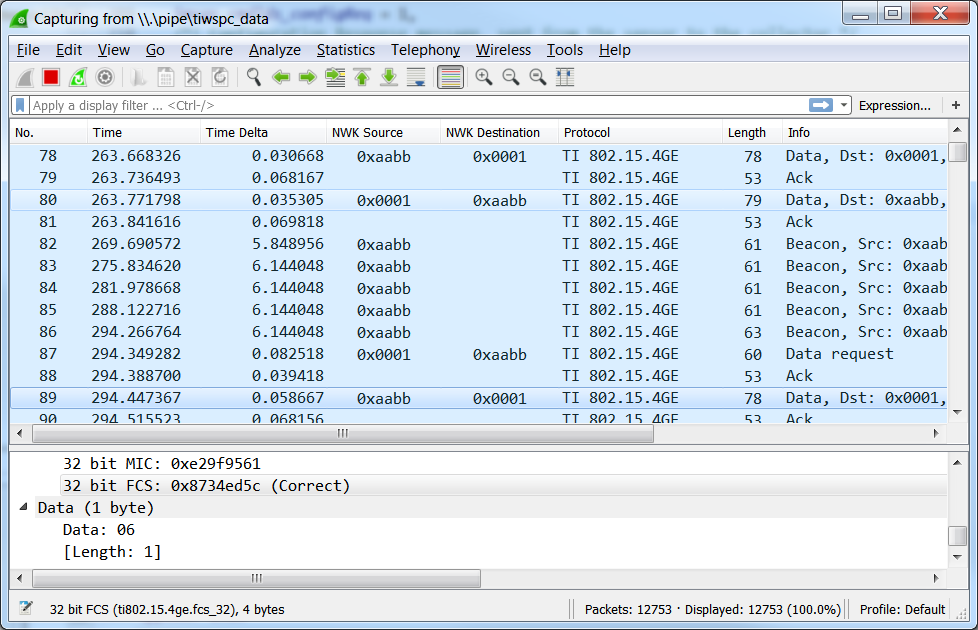
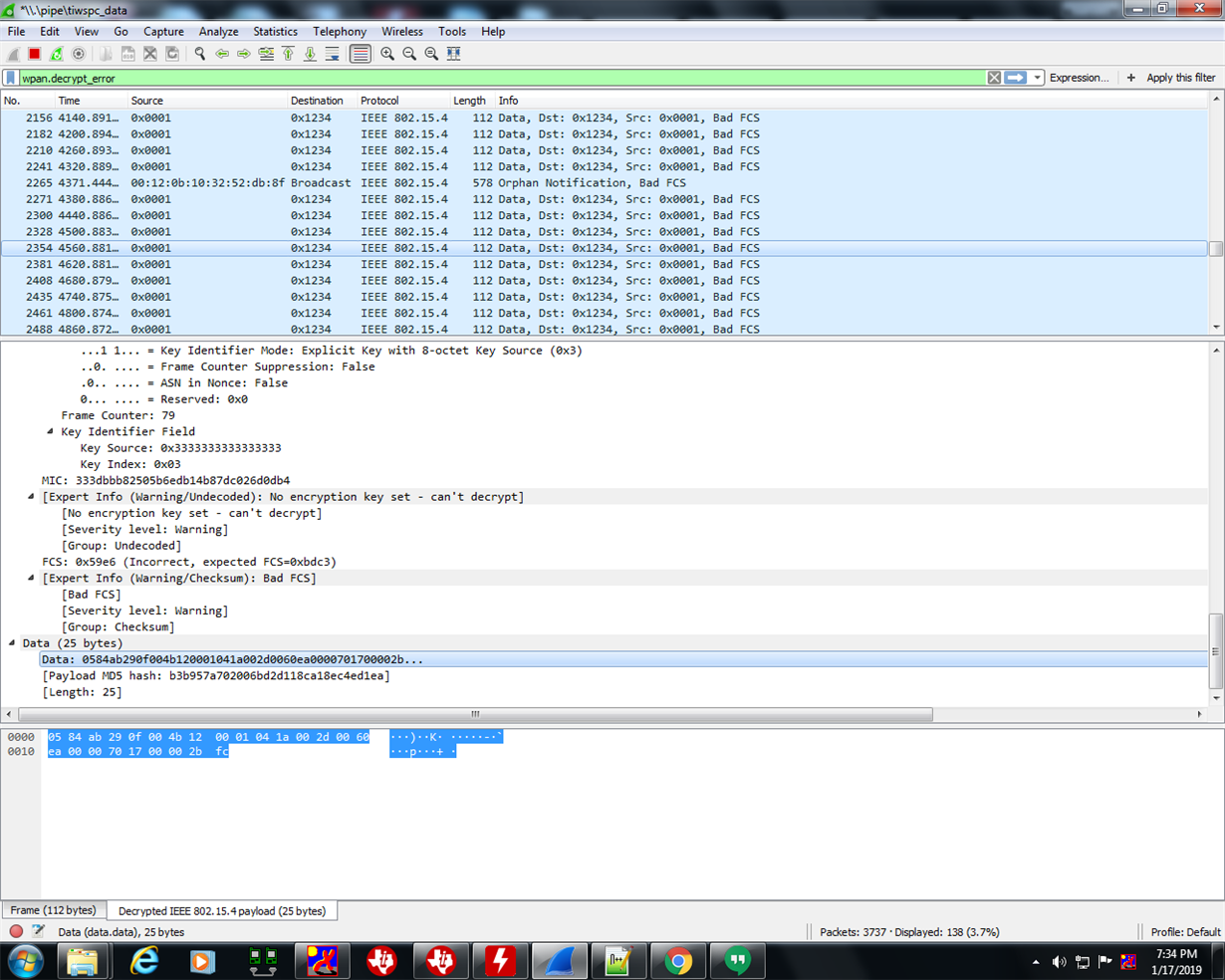
I am workin on security under TI 15.4 stack. I want to validate whether the encrypted packets which are being sent to the collector using packet sniffer.
My main role is to validate the encrypted packets by decrypting it by any means and comparing it with the actual data.
I have found aesccm and aesesb code in resource explorer.
1) i want to know whats the difference between two codes.
2) i want to use either of these two codes on CC1350 launchpad, how?
Thank you.