Hi,
Since a few days ago we are having some issues with our azure server closing the connection abruptly.
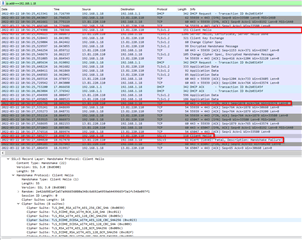
Normally the mechanism in HTTPClient_sendRequest retries to open a connection. However during this reconnection the security attributes is not set as expected.
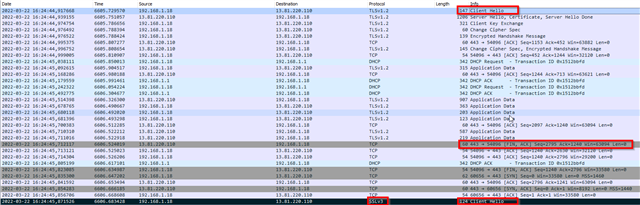
Here is a wireshark capture which shows the initial connection with TLS1.2, the FIN,ACK sent by the server, and the new connection initiated by the cc3235 with SSLv3 instead of TLS1.2. It also did not use the cipher setting for the reconnection.
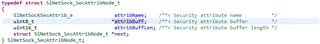
I'm trying to modify httpclient, but have not found how to correct this behavior. SlNetSock_startSec is correctly called on the retry and with the correct secAttribs
What could lead to the security attributes being ignored?
Note: I'm using last sdk/service pack.