Other Parts Discussed in Thread: UNIFLASH
Hi,
We have an application with an OTA mechanism implemented. Since our current code signing certificate is about to expire, we have requested a new.
Our certificate authority does not support the SHA 256 key size anymore and supplied a new 512 key size.
This new key trow an error in our OTA application, we tracked this down to the sl_FsClose function.
When using our new key the function returns -10290
#define SL_ERROR_FS_WRONG_SIGNATURE_OR_CERTIFIC_NAME_LENGTH (-10290L)
If we check the Simplelink WiFi Network processor user guide we find on page 138 chapter 8.4.7 there is noted that the device supports up to 512 certificate chain verification type.
https://www.ti.com/lit/ug/swru455m/swru455m.pdf?ts=1665048047843
Another test we did, is that we flashed the device with an image, signed with the old certificate, containing the necessary files to support the new certificate. But we still getting the sl_FsCl.ose error after performing an OTA.
When we try to flash the device using Uniflash we get the error below:
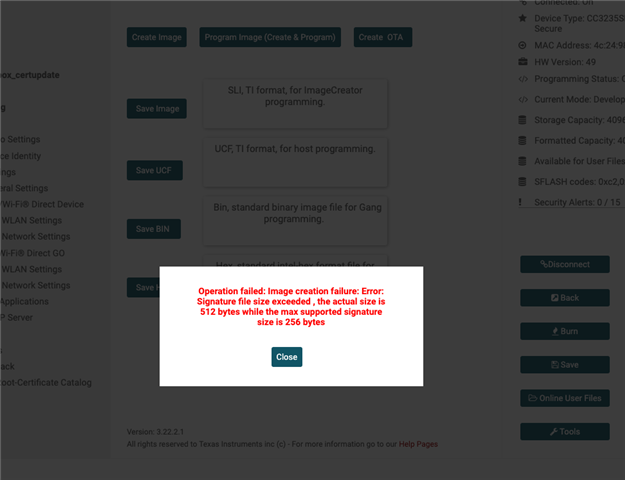
We tested both ways (OTA and Uniflash) with sp_4.8.0.8_3.7.0.1_3.1.0.26, and sp_4.13.0.2_3.7.0.1_3.1.0.26