Other Parts Discussed in Thread: CC3235SF
I'm working with prototype based on mqtt_client_over_tls_1_3_CC3235SF_LAUNCHXL_tirtos7_ticlang example. SDK used is simplelink_cc32xx_sdk_7_10_00_13. For prototyping was used https://test.mosquitto.org/ public broker. Successfully got TLS 1.3 connection to port public broker on port 8883: MQTT, encrypted, unauthenticated. On next step I tried to connect to port 8884: MQTT, encrypted, client certificate required. And start getting issues. During debugging it found out, that connection was failed with "0x7780 SSL - A fatal alert message was received from our peer" error code. Enabling tracing gave me a reason: Alert message was 116. Means, that server waits for out certificate. trying to figure out, why certificate was not send to server, rebuilder mbedtls library to get debug symbols and found, that there was not set own certificates. Find out, that certificates should be set with mbedtls_ssl_conf_own_cert(&pTlsSock->ssl.conf, &pTlsSock->srvcert, &pTlsSock->pkey) function. After setting certificates up got device crush. With following error:
Cortex_M4_0: Can't Run Target CPU: (Error -1268 @ 0x1090001) Device is locked up in Hard Fault or in NMI. Reset the device, and retry the operation. If error persists, confirm configuration, power-cycle the board, and/or try more reliable JTAG settings (e.g. lower TCLK). (Emulation package 9.11.0.00128) Cortex_M4_0: Can't Run Target CPU: (Error -1268 @ 0x1090001) Device is locked up in Hard Fault or in NMI. Reset the device, and retry the operation. If error persists, confirm configuration, power-cycle the board, and/or try more reliable JTAG settings (e.g. lower TCLK). (Emulation package 9.11.0.00128)
Some more debugging bring following point of failure:
It is an eighth call of following function:
psa_status_t mbedtls_psa_external_get_random( mbedtls_psa_external_random_context_t *context,
uint8_t *output,
size_t output_size,
size_t *output_length)
{
int status;
unsigned short length;
length = (unsigned short)output_size;
status = sl_NetUtilGet(SL_NETUTIL_TRUE_RANDOM,0,output,&(length));
if (status==0)
{
*output_length = output_size;
}
return status;
}
There we can find actual call-stack before failure: 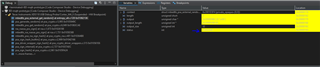
And core registers state as well: 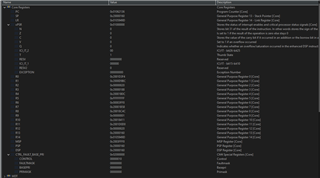
What should be done to perform proper authenticated TLS1.3 connection?

