Tool/software:
We've got reports from customers running one of our devices with the WL1831 chipset that the CPU was highly affected by the wifi network causing a Denial of Service on the device. Upon closer inspection it was seen that the devices were getting flooded by ICMP broadcast packets which caused the IRQ line to go high continuously and the kernel having to manage all the traffic.

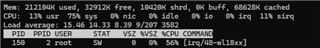
We have the same device in production running also a Broadcom chipset which does not behave the same way. The only difference here is the chipset, the wifi firmware and the driver. All the other parts of the Linux system is identical.
Therefore, we are investigating if there is a configuration option on the driver level which we could trigger to have the wifi firmware filter out these messages better?
We are running with the driver in mainline linux kernel 6.1.126 together with wl18xx-fw firmware 8.9.1.0.2.

