Tool/software:
Dear Shlomi
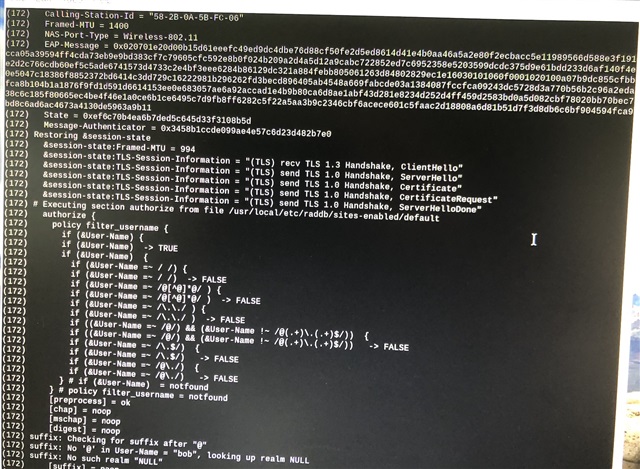
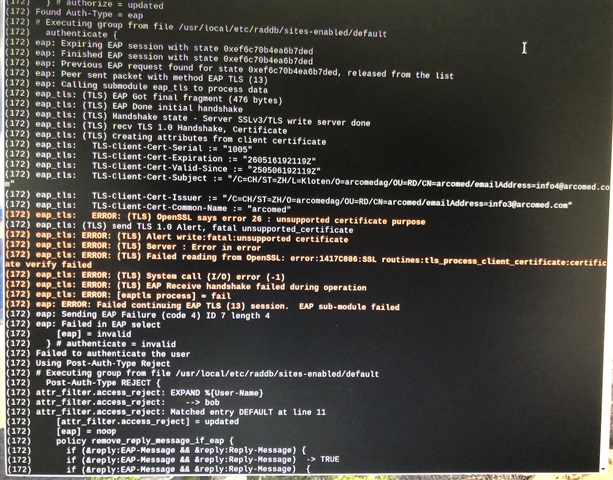
Regarding the authentication with an intermediate AND root CA to a RADIUS server we still are not able to connect.
Can you confirm:
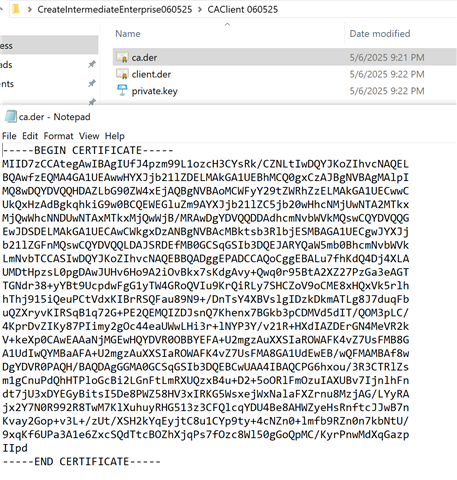
- Both the intermediate and root CA are stored in the same file ca.der in the PEM format (see also screenshot)?
- Only one ca.der file is stored in the sys/cert folder (with both certificates in the same file)?
folder (with both certificates in the same file)?
- The CC3235 will then go automatically though all certificates stored in that one file?
Many thanks
Marc